Question 141
A security administrator is concerned about employees connecting their personal devices to the company network. Doing so is against company policy. The network does not have a NAC solution. The company uses a GPO that disables the firewall on all company-owned devices while they are connected to the internal network Additionally, all company-owned devices implement a standard naming convention that uses the device's serial number. The security administrator wants to identify active personal devices and write a custom script to disconnect them from the network Which of the following should the script use to BEST accomplish this task?
Question 142
A security engineer is assessing the controls that are in place to secure the corporate-Internet-facing DNS server. The engineer notices that security ACLs exist but are not being used properly. The DNS server should respond to any source but only provide information about domains it has authority over. Additionally, the DNS administrator have identified some problematic IP addresses that should not be able to make DNS requests. Given the ACLs below:
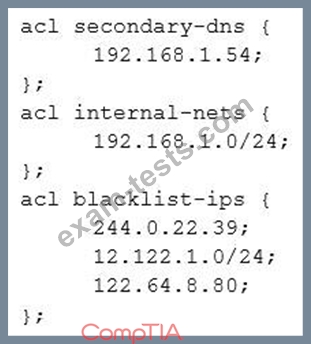
Which of the following should the security administrator configure to meet the DNS security needs?
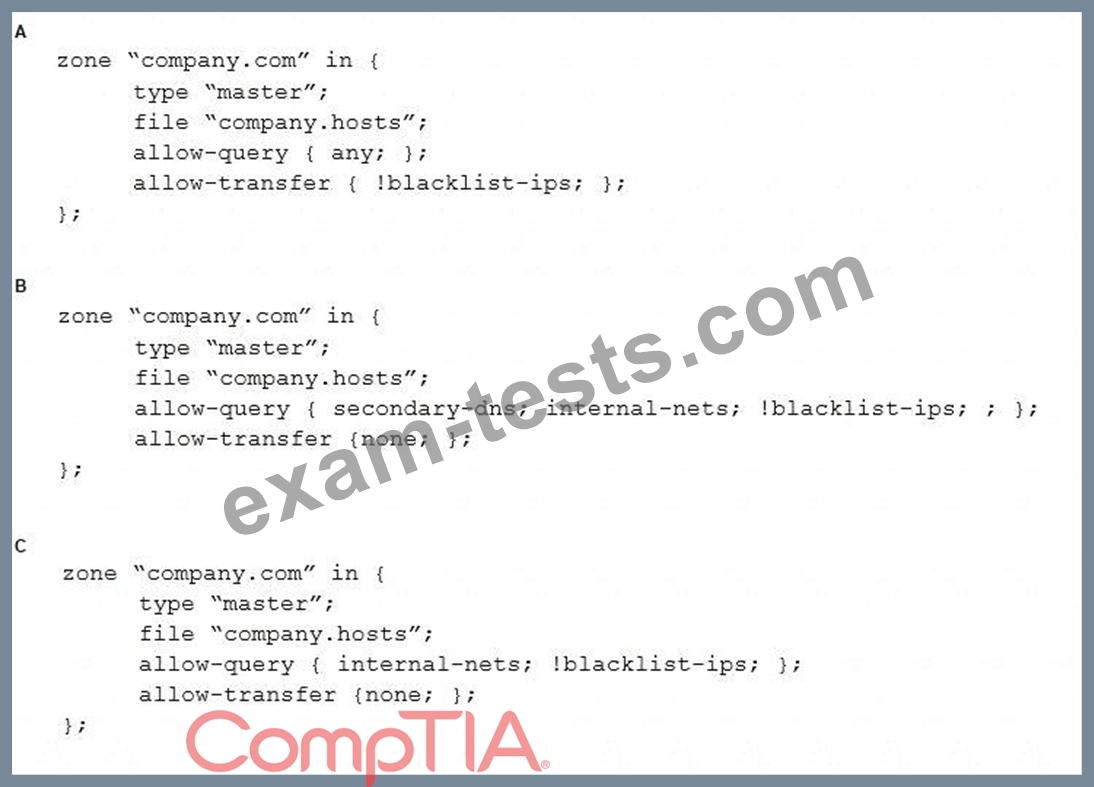
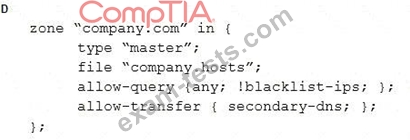

Which of the following should the security administrator configure to meet the DNS security needs?


Question 143
As a result of an acquisition, a new development team is being integrated into the company. The
development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize
SaaS. To have the team up and running effectively, a separate Internet connection has been procured.
A stand up has identified the following additional requirements:
1. Reuse of the existing network infrastructure
2. Acceptable use policies to be enforced
3. Protection of sensitive files
4. Access to the corporate applications
Which of the following solution components should be deployed to BEST meet the requirements? (Select
three.)
development team has BYOD laptops with IDEs installed, build servers, and code repositories that utilize
SaaS. To have the team up and running effectively, a separate Internet connection has been procured.
A stand up has identified the following additional requirements:
1. Reuse of the existing network infrastructure
2. Acceptable use policies to be enforced
3. Protection of sensitive files
4. Access to the corporate applications
Which of the following solution components should be deployed to BEST meet the requirements? (Select
three.)
Question 144
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation-states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
Question 145
The Chief Information Officer (CIO) is focused on improving IT governance within the organization to reduce system downtime.
The CIO has mandated that the following improvements be implemented:
- All business units must now identify IT risks and include them in
their business risk profiles.
- Key controls must be identified and monitored.
- Incidents and events must be recorded and reported with management
oversight.
- Exemptions to the information security policy must be formally
recorded, approved, and managed.
- IT strategy will be reviewed to ensure it is aligned with the
businesses strategy and objectives.
In addition to the above, which of the following would BEST help the CIO meet the requirements?
The CIO has mandated that the following improvements be implemented:
- All business units must now identify IT risks and include them in
their business risk profiles.
- Key controls must be identified and monitored.
- Incidents and events must be recorded and reported with management
oversight.
- Exemptions to the information security policy must be formally
recorded, approved, and managed.
- IT strategy will be reviewed to ensure it is aligned with the
businesses strategy and objectives.
In addition to the above, which of the following would BEST help the CIO meet the requirements?

