Question 111
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside
cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the
following:
High-impact controls implemented: 6 out of 10

Medium-impact controls implemented: 409 out of 472

Low-impact controls implemented: 97 out of 1000

The report includes a cost-benefit analysis for each control gap. The analysis yielded the following
information:
Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control

gap: $95,000
Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact

control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of
the medium-impact controls will take two years to fully implement. Which of the following conclusions could
the CISO draw from the analysis?
cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the
following:
High-impact controls implemented: 6 out of 10

Medium-impact controls implemented: 409 out of 472

Low-impact controls implemented: 97 out of 1000

The report includes a cost-benefit analysis for each control gap. The analysis yielded the following
information:
Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control

gap: $95,000
Average medium-impact control implementation cost: $6,250; Probable ALE for each medium-impact

control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than 50% of
the medium-impact controls will take two years to fully implement. Which of the following conclusions could
the CISO draw from the analysis?
Question 112
Management is reviewing the results of a recent risk assessment of the organization's policies and procedures.
During the risk assessment it is determined that procedures associated with background checks have not been effectively implemented. In response to this risk, the organization elects to revise policies and procedures related to background checks and use a third-party to perform background checks on all new employees.
Which of the following risk management strategies has the organization employed?
During the risk assessment it is determined that procedures associated with background checks have not been effectively implemented. In response to this risk, the organization elects to revise policies and procedures related to background checks and use a third-party to perform background checks on all new employees.
Which of the following risk management strategies has the organization employed?
Question 113
The Chief Executive Officer (CEO) of a large prestigious enterprise has decided to reduce business costs by outsourcing to a third party company in another country. Functions to be outsourced include: business analysts, testing, software development and back office functions that deal with the processing of customer data. The Chief Risk Officer (CRO) is concerned about the outsourcing plans. Which of the following risks are MOST likely to occur if adequate controls are not implemented?
Question 114
After analyzing code, two developers al a company bring these samples to the security operations manager.
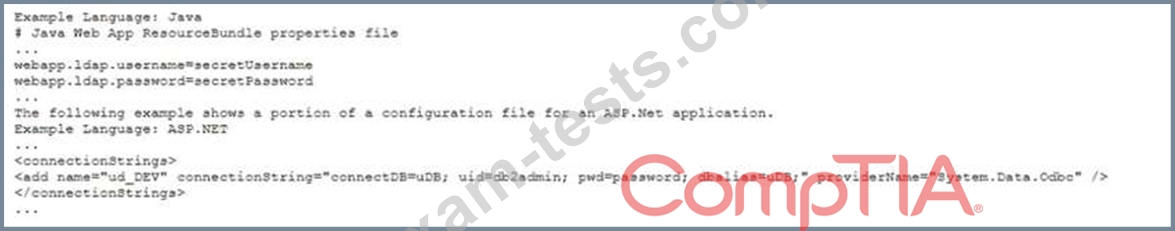
Which of the following would BEST solve these coding problems?

Which of the following would BEST solve these coding problems?
Question 115
A large organization has recently suffered a massive credit card breach. During the months of Incident Response, there were multiple attempts to assign blame for whose fault it was that the incident occurred. In which part of the incident response phase would this be addressed in a controlled and productive manner?

