Question 126
Two competing companies experienced similar attacks on their networks from various threat actors. To improve response times, the companies wish to share some threat intelligence about the sources and methods of attack.
Which of the following business documents would be BEST to document this engagement?
Which of the following business documents would be BEST to document this engagement?
Question 127
The Chief Information Officer (CIO) has been asked to develop a security dashboard with the relevant
metrics. The board of directors will use the dashboard to monitor and track the overall security posture of
the organization. The CIO produces a basic report containing both KPI and KRI data in two separate
sections for the board to review.
Which of the following BEST meets the needs of the board?
metrics. The board of directors will use the dashboard to monitor and track the overall security posture of
the organization. The CIO produces a basic report containing both KPI and KRI data in two separate
sections for the board to review.
Which of the following BEST meets the needs of the board?
Question 128
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on their network. Vendors were authenticating directly to the retailer's AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept. The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that because the vendors were required to have site to site VPN's no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
Question 129
A security administrator wants to implement an MDM solution to secure access to company email and files in a BYOD environment. The solution must support the following requirements:
* Company administrators should not have access to employees' personal information.
* A rooted or jailbroken device should not have access to company sensitive information.
Which of the following BEST addresses the associated risks?
* Company administrators should not have access to employees' personal information.
* A rooted or jailbroken device should not have access to company sensitive information.
Which of the following BEST addresses the associated risks?
Question 130
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following:
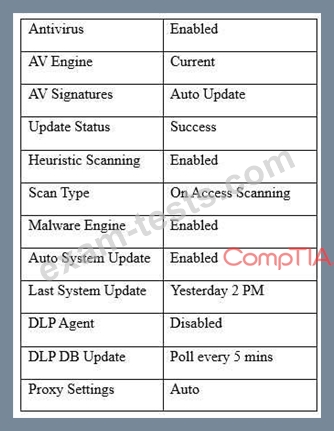
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

