Question 146
During an incident involving the company main database, a team of forensics experts is hired to respond to the breach. The team is in charge of collecting forensics evidence from the company's database server. Which of the following is the correct order in which the forensics team should engage?
Question 147
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
Question 148
As a security administrator, you areasked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server.
There are no wireless connections to the server, and it does not needto print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
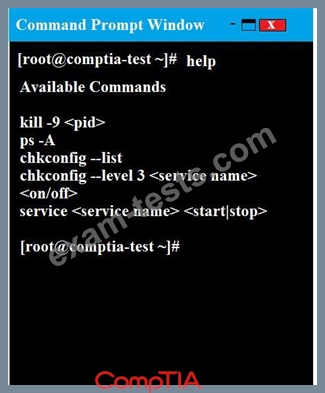
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It ispossible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server.
There are no wireless connections to the server, and it does not needto print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It ispossible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 149
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following:
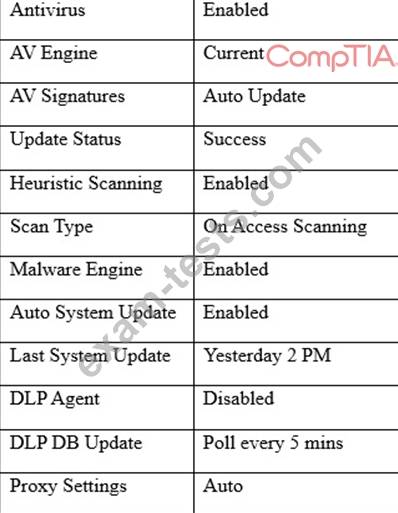
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Question 150
The SOC is reviewing processes and procedures after a recent incident. The review indicates it took more than 30 minutes to determine that quarantining an infected host was the best course of action. This allowed the malware to spread to additional hosts before it was contained. Which of the following would BEST to improve the incident response process?

