Question 96
An analyst is examining a system that is suspected of being involved in an intrusion. The analyst uses the command 'cat/etc/passwd' and receives the following partial output:
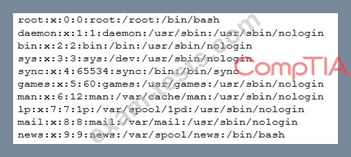
Based on the above output, which of the following should the analyst investigate further?

Based on the above output, which of the following should the analyst investigate further?
Question 97
Which of the following policies BEST explains the purpose of a data ownership policy?
Question 98
A cybersecurity analyst traced the source of an attack to compromised user credentials.
Log analysis revealed that the attacker successfully authenticated from an unauthorized foreign country. Management asked the security analyst to research and implement a solution to help mitigate attacks based on compromised passwords. Which of the following should the analyst implement?
Log analysis revealed that the attacker successfully authenticated from an unauthorized foreign country. Management asked the security analyst to research and implement a solution to help mitigate attacks based on compromised passwords. Which of the following should the analyst implement?
Question 99
Alerts have been received from the SIEM, indicating infections on multiple computers. Based on threat
characteristics, these files were quarantined by the host-based antivirus program. At the same time,
additional alerts in the SIEM show multiple blocked URLs from the address of the infected computers; the
URLs were classified as uncategorized. The domain location of the IP address of the URLs that were
blocked is checked, and it is registered to an ISP in Russia. Which of the following steps should be taken
NEXT?
characteristics, these files were quarantined by the host-based antivirus program. At the same time,
additional alerts in the SIEM show multiple blocked URLs from the address of the infected computers; the
URLs were classified as uncategorized. The domain location of the IP address of the URLs that were
blocked is checked, and it is registered to an ISP in Russia. Which of the following steps should be taken
NEXT?
Question 100
After running a packet analyzer on the network, a security analyst has noticed the following output:
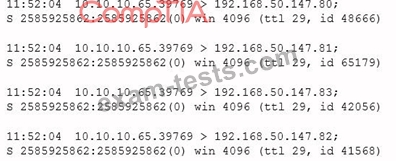
Which of the following is occurring?

Which of the following is occurring?

