Question 81
A network technician is concerned that an attacker is attempting to penetrate the network, and wants to set a rule on the firewall to prevent the attacker from learning which IP addresses are valid on the network.
Which of the following protocols needs to be denied?
Which of the following protocols needs to be denied?
Question 82
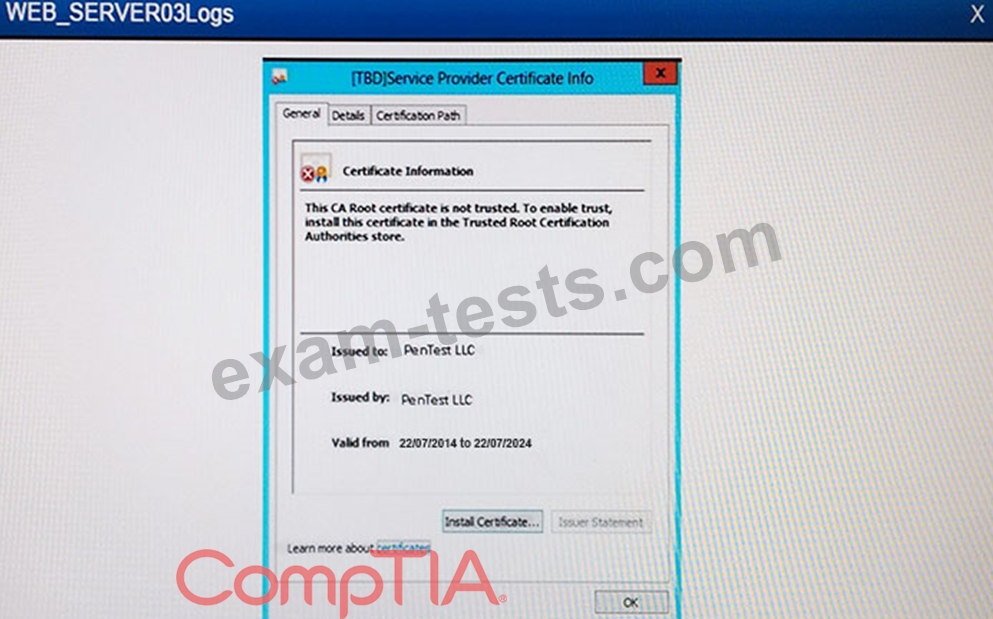
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS. If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean. If the vulnerability is valid, the analyst must remediate the finding. After reviewing the given information, select the STEP 2 tab in order to complete the simulation by selecting the correct "Validation Result" AND "Remediation Action" for each server listed using the drop down options.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
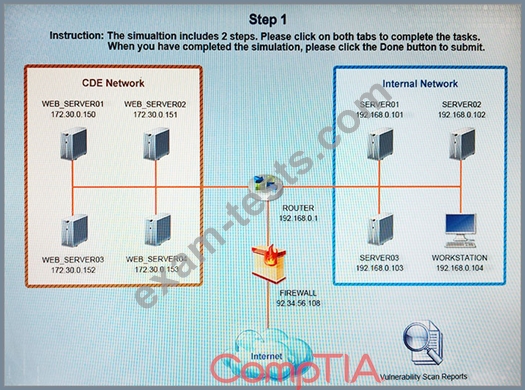

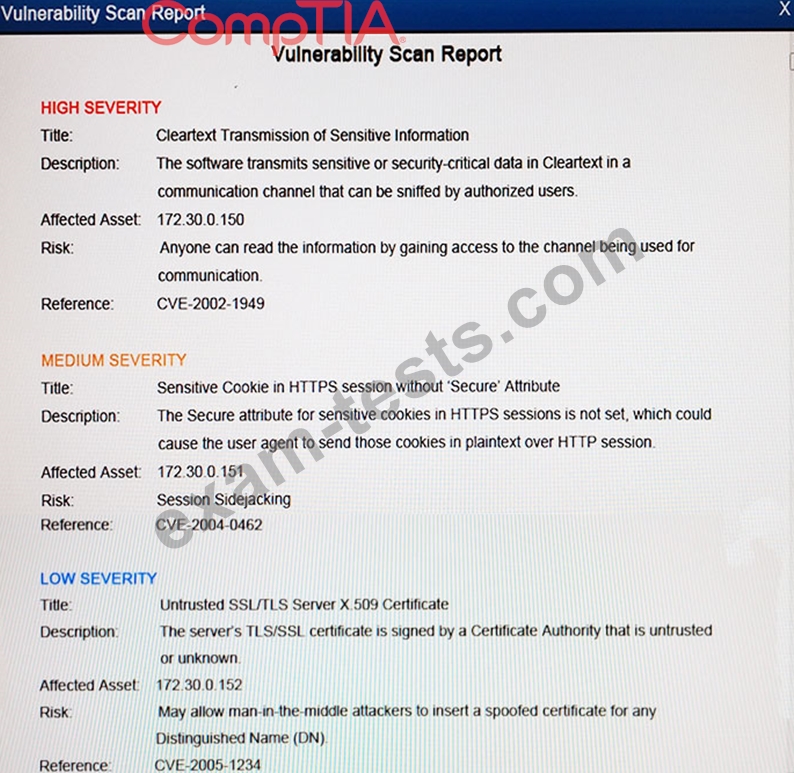
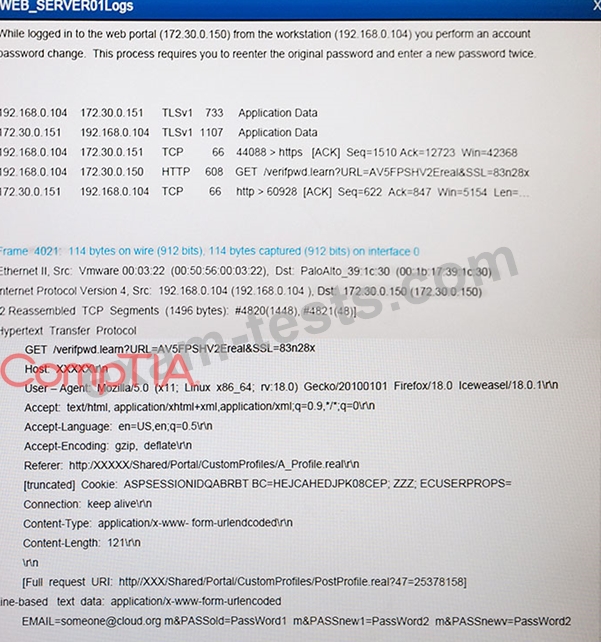
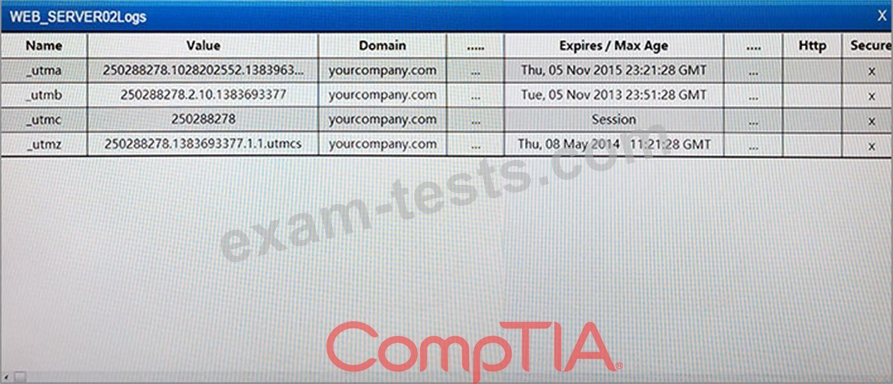
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.






Question 83
A security analyst is assisting with a computer crime investigator and has been asked to secure a PC and deliver it to the forensics lab. Which of the following items would be MOST helpful to secure the PC (Select THREE)
Question 84
Several users have reported that when attempting to save documents in team folders, the following message is received:
The File Cannot Be Copied or Moved - Service Unavailable.
Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
The File Cannot Be Copied or Moved - Service Unavailable.
Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
Question 85
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?

