Question 91
A manufacturing company has decided to participate in direct sales of its products to consumers. The company decides to use a subdomain of its main site with its existing cloud service provider as the portal for e-commerce. After launch, the site is stable and functions properly, but after a robust day of sales, the site begins to redirect to a competitor's landing page. Which of the following actions should the company's security team take to determine the cause of the issue and minimize the scope of impact?
Question 92
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized
activities. Which of the following documents should include these details?
activities. Which of the following documents should include these details?
Question 93
A company installed a wireless network more than a year ago, standardizing on the same model APs in a
single subnet. Recently, several users have reported timeouts and connection issues with Internet
browsing. The security administrator has gathered some information about the network to try to recreate
the issues with the assistance of a user. The administrator is able to ping every device on the network and
confirms that the network is very slow.
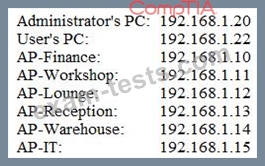
Output:
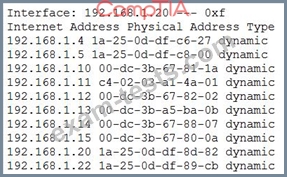
Given the above results, which of the following should the administrator investigate FIRST?
single subnet. Recently, several users have reported timeouts and connection issues with Internet
browsing. The security administrator has gathered some information about the network to try to recreate
the issues with the assistance of a user. The administrator is able to ping every device on the network and
confirms that the network is very slow.

Output:

Given the above results, which of the following should the administrator investigate FIRST?
Question 94
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
Question 95
Oven the following log snippet:
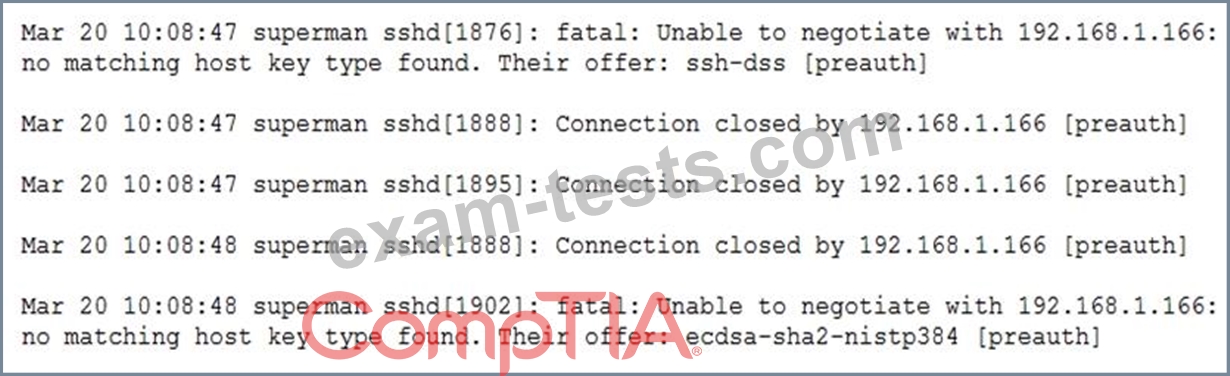
Which of the following describes the events that have occurred?

Which of the following describes the events that have occurred?

