Question 86
A security professional is analyzing the results of a network utilization report. The report includes the following information:
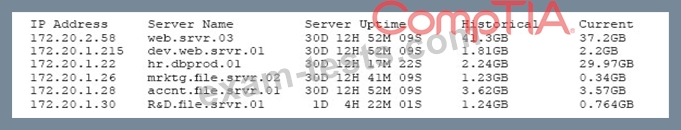
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?
Question 87
A logistics company's vulnerability scan identifies the following vulnerabilities on Internet-facing devices in
the DMZ:
SQL injection on an infrequently used web server that provides files to vendors

SSL/TLS not used for a website that contains promotional information

The scan also shows the following vulnerabilities on internal resources:
Microsoft Office Remote Code Execution on test server for a human resources system

TLS downgrade vulnerability on a server in a development network

In order of risk, which of the following should be patched FIRST?
the DMZ:
SQL injection on an infrequently used web server that provides files to vendors

SSL/TLS not used for a website that contains promotional information

The scan also shows the following vulnerabilities on internal resources:
Microsoft Office Remote Code Execution on test server for a human resources system

TLS downgrade vulnerability on a server in a development network

In order of risk, which of the following should be patched FIRST?
Question 88
Various devices are connecting and authenticating to a single evil twin within the network. Which of the following are MOST likely being targeted?
Question 89
An organization has two environments: development and production. Development is where applications are developed with unit testing. The development environment has many configuration differences from the production environment. All applications are hosted on virtual machines. Vulnerability scans are performed against all systems before and after any application or configuration changes to any environment. Lately, vulnerability remediation activity has caused production applications to crash and behave unpredictably.
Which of the following changes should be made to the current vulnerability management process?
Which of the following changes should be made to the current vulnerability management process?
Question 90
Which of the following describes why it is important to include scope within the rules of engagement of a penetration test?

