Question 76
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
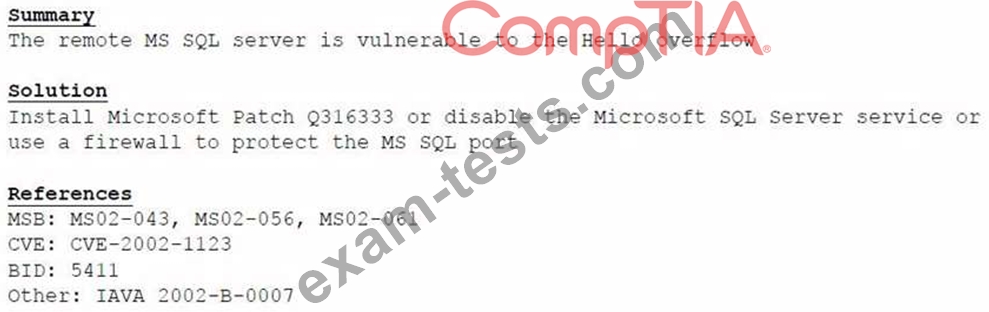
Based on the above information, which of the following should the system administrator do? (Select TWO).

Based on the above information, which of the following should the system administrator do? (Select TWO).
Question 77
A recent audit included a vulnerability scan that found critical patches released 60 days prior were not applied to servers in the environment. The infrastructure team was able to isolate the issue and determined it was due to a service being disabled on the server running the automated patch management application.
Which of the following would be the MOST efficient way to avoid similar audit findings in the future?
Which of the following would be the MOST efficient way to avoid similar audit findings in the future?
Question 78
An analyst is observing unusual network traffic from a workstation. The workstation is communicating with a known malicious site over an encrypted tunnel. A full antivirus scan with an updated antivirus signature file does not show any sign of infection. Which of the following has occurred on the workstation?
Question 79
A software assurance lab is performing a dynamic assessment on an application by automatically
generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of
the following software assessment capabilities is the lab performing AND during which phase of the SDLC
should this occur? (Select two.)
generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of
the following software assessment capabilities is the lab performing AND during which phase of the SDLC
should this occur? (Select two.)
Question 80
Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company A's conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company B's network. The security architect for Company A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?

