Question 121
As part of the SDLC, software developers are testing the security of a new web application by inputting
large amounts of random data. Which of the following types of testing is being performed?
large amounts of random data. Which of the following types of testing is being performed?
Question 122
Which of the following could be directly impacted by an unpatched vulnerability m vSphre ESXi?
Question 123
A threat intelligence analyst who works for a financial services firm received this report:
"There has been an effective waterhole campaign residing at
www.bankfinancecompsoftware.com. This domain is delivering ransomware. This ransomware variant has been called "LockMaster" by researchers due to its ability to overwrite the MBR, but this term is not a malware signature. Please execute a defensive operation regarding this attack vector." The analyst ran a query and has assessed that this traffic has been seen on the network.
Which of the following actions should the analyst do NEXT? (Select TWO).
"There has been an effective waterhole campaign residing at
www.bankfinancecompsoftware.com. This domain is delivering ransomware. This ransomware variant has been called "LockMaster" by researchers due to its ability to overwrite the MBR, but this term is not a malware signature. Please execute a defensive operation regarding this attack vector." The analyst ran a query and has assessed that this traffic has been seen on the network.
Which of the following actions should the analyst do NEXT? (Select TWO).
Question 124
A security analyst is conducting a vulnerability assessment of older SCADA devices on the corporate network.
Which of the following compensating controls is likely to prevent the scans from providing value?
Which of the following compensating controls is likely to prevent the scans from providing value?
Question 125
A cybersecurity analyst is reviewing the following outputs:
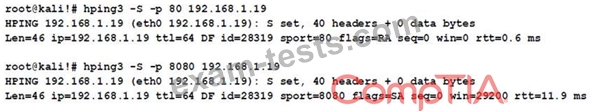
Which of the following can the analyst infer from the above output?

Which of the following can the analyst infer from the above output?

