Question 141
An organization subscribes to multiple third-party security intelligence feeds. It receives a notification from one of these feeds indicating a zero-day malware attack is impacting the SQL server prior to SP 2. The notification also indicates that infected systems attempt to communicate to external IP addresses on port 2718 to download additional payload. After consulting with the organization's database administrator, it is determined that there are several SQL servers that are still on SP 1, and none of the SQL servers would normally communicate over port 2718. Which of the following is the BEST mitigation step to implement until the SQL servers can be upgraded to SP 2 with minimal impact to the network?
Question 142
A system administrator has reviewed the following output:
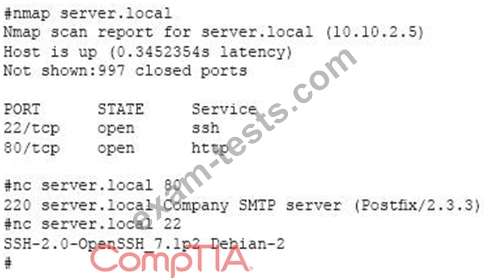
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
Question 143
A cybersecurity analyst is reviewing the current BYOD security posture. The users must be able to synchronize their calendars, email, and contacts to a smartphone or other personal device. The recommendation must provide the most flexibility to users. Which of the following recommendations would meet both the mobile data protection efforts and the business requirements described in this scenario?
Question 144
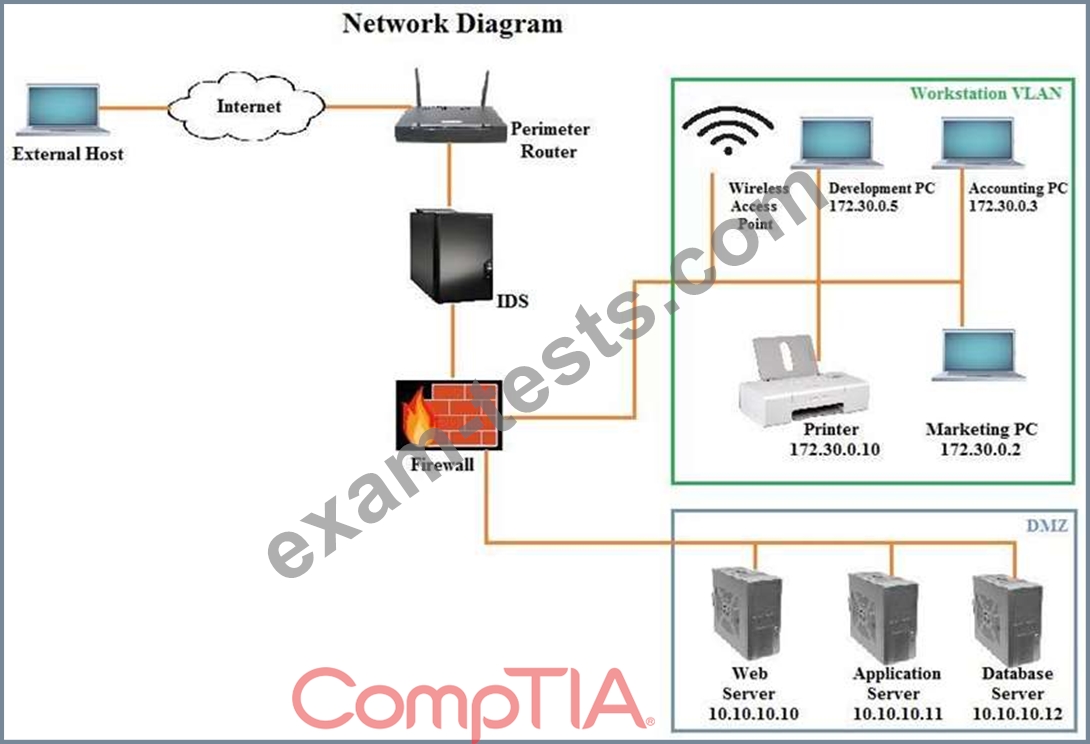
You suspect that multiple unrelated security events have occurred on several nodes on a corporate network.
You must review all logs and correlate events when necessary to discover each security event by clicking on each node. Only select corrective actions if the logs shown a security event that needs remediation. Drag and drop the appropriate corrective actions to mitigate the specific security event occurring on each affected device.
Instructions:
The Web Server, Database Server, IDS, Development PC, Accounting PC and Marketing PC are clickable.
Some actions may not be required and each actions can only be used once per node. The corrective action order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
You must review all logs and correlate events when necessary to discover each security event by clicking on each node. Only select corrective actions if the logs shown a security event that needs remediation. Drag and drop the appropriate corrective actions to mitigate the specific security event occurring on each affected device.
Instructions:
The Web Server, Database Server, IDS, Development PC, Accounting PC and Marketing PC are clickable.
Some actions may not be required and each actions can only be used once per node. The corrective action order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.


Question 145
During the forensic phase of a security investigation, it was discovered that an attacker was able to find private keys on a poorly secured team shared drive. The attacker used those keys to intercept and decrypt sensitive traffic on a web server. Which of the following describes this type of exploit and the potential remediation?