Question 136
A company's IDP/DLP solution triggered the following alerts:
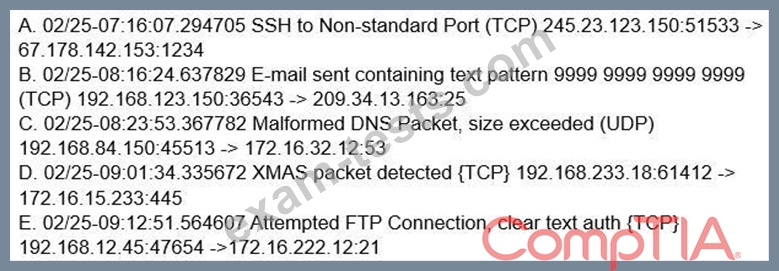
Which of the following alerts should a security analyst investigate FIRST?

Which of the following alerts should a security analyst investigate FIRST?
Question 137
An organization has been conducting penetration testing to identify possible network vulnerabilities. One of the security policies states that web servers and database servers must not be co-located on the same server unless one of them runs on a non-standard. The penetration tester has received the following outputs from the latest set of scans:
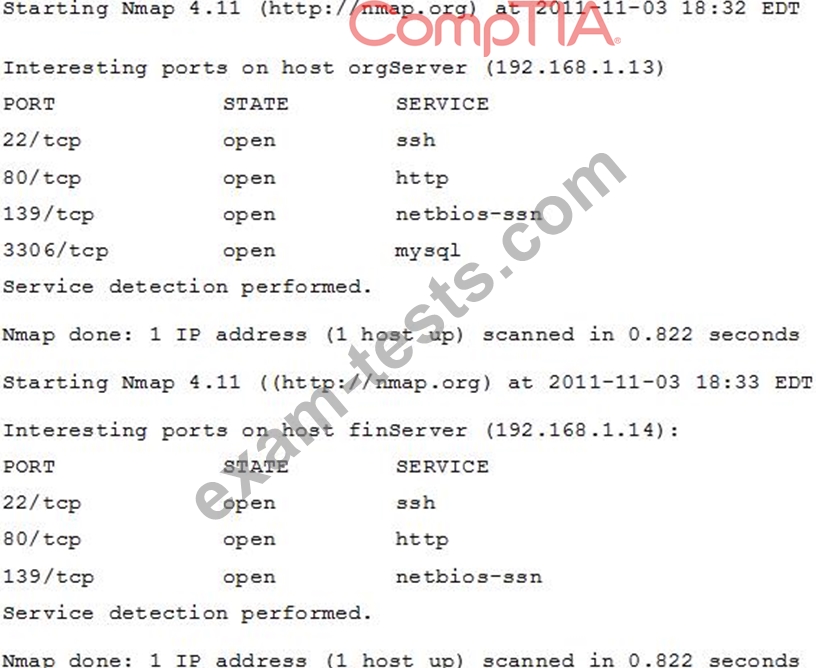
Which of the following servers is out of compliance?

Which of the following servers is out of compliance?
Question 138
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
Question 139
Which of the following best practices is used to identify areas in the network that may be vulnerable to penetration testing from known external sources?
Question 140
A security analyst has been asked to scan a subnet. During the scan, the following output was generated:
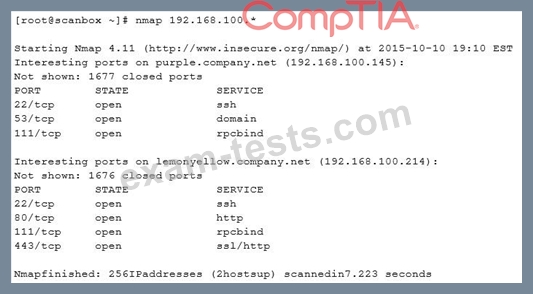
Based on the output above, which of the following is MOST likely?

Based on the output above, which of the following is MOST likely?

