Question 126
A technician is troubleshooting a desktop computer with low disk space. The technician reviews the following information snippets:

Which of the following should the technician do to BEST resolve the issue based on the above information? (Choose two.)

Which of the following should the technician do to BEST resolve the issue based on the above information? (Choose two.)
Question 127
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets:
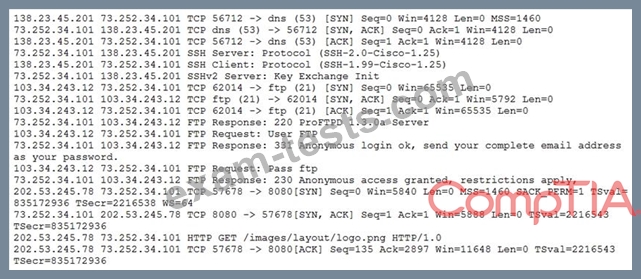
Which of the following traffic patterns or data would be MOST concerning to the security analyst?

Which of the following traffic patterns or data would be MOST concerning to the security analyst?
Question 128
A company's IDP/DLP solution triggered the following alerts:
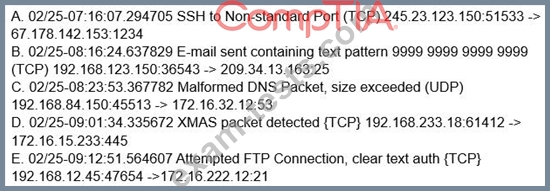
Which of the following alerts should a security analyst investigate FIRST?

Which of the following alerts should a security analyst investigate FIRST?
Question 129
A cybersecurity analyst is conducting packet analysis on the following:
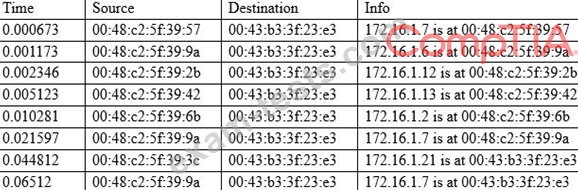
Which of the following is occurring in the given packet capture?

Which of the following is occurring in the given packet capture?
Question 130
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions. Which of the following technologies meet the compatibility requirement? (Select three.)

