Question 146
Server contains baseline images that are deployed to sensitive workstations on a regular basis. The images are evaluated once per month for patching and other fixes, but do not change otherwise. Which of the following controls should be put in place to secure the file server and ensure the images are not changed?
Question 147
During a recent audit, there were a lot of findings similar to and including the following:
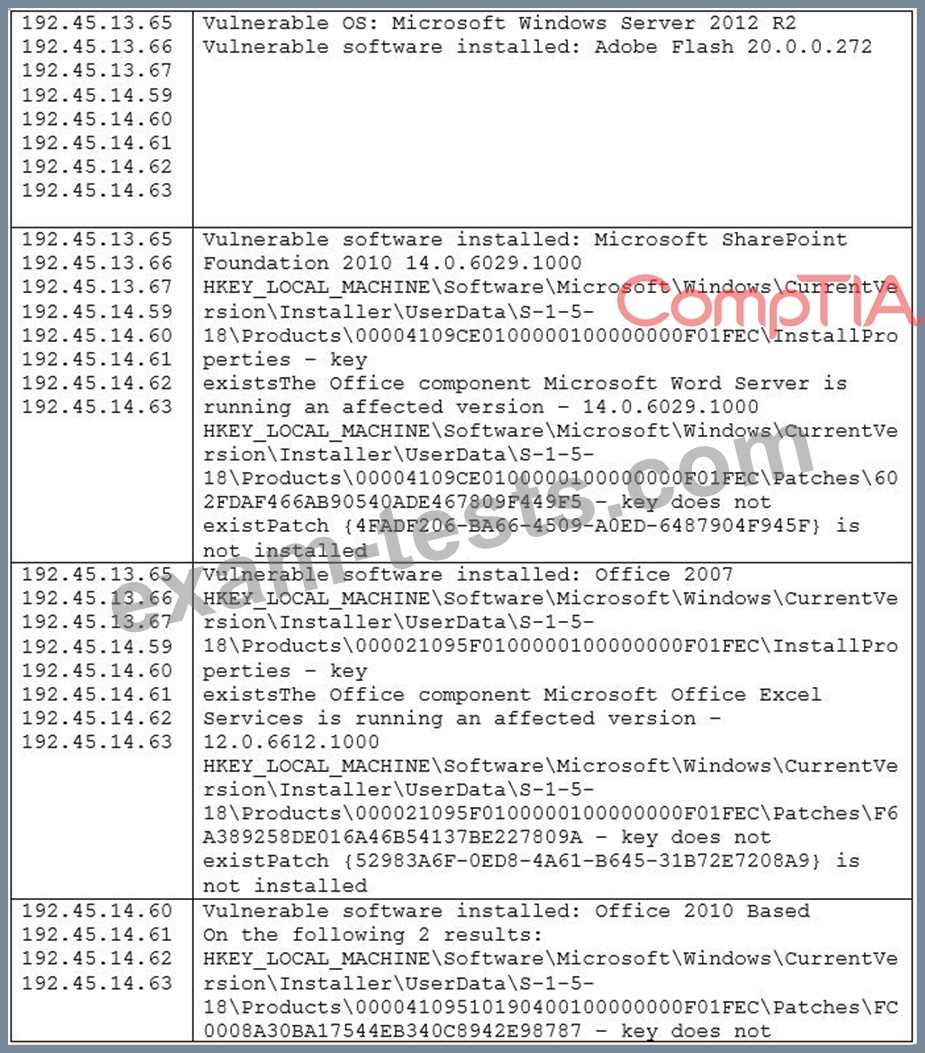
Which of the following would be the BEST way to remediate these findings and minimize similar findings in
the future?

Which of the following would be the BEST way to remediate these findings and minimize similar findings in
the future?
Question 148
Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company A's conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company B's network. The security architect for Company
A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?
A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?
Question 149
File integrity monitoring states the following files have been changed without a written request or approved
change. The following change has been made:
chmod 777 -Rv /usr
Which of the following may be occurring?
change. The following change has been made:
chmod 777 -Rv /usr
Which of the following may be occurring?
Question 150
A cybersecurity analyst is conducting packet analysis on the following:
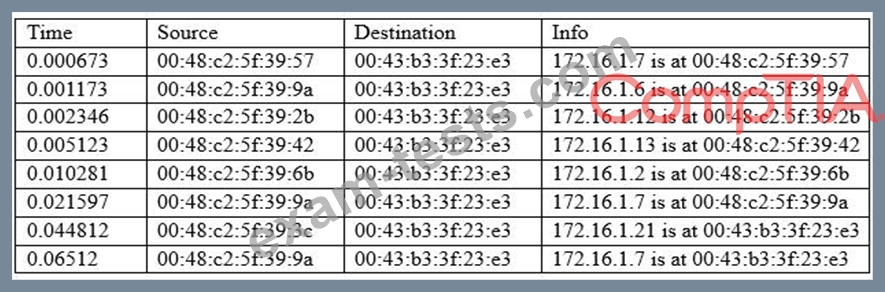
Which of the following is occurring in the given packet capture?

Which of the following is occurring in the given packet capture?

