Question 151
A cybersecurity analyst is hired lo review lite security measures implemented within the domain controllers of a company Upon review, me cybersecurity analyst notices a brute force attack can be launched against domain controllers thai run on a Windows platform The first remediation step implemented by the cybersecurity analyst Is to make the account passwords more complex Which of the following Is the NEXI remediation step the cybersecurity analyst needs to implement?
Question 152
An analyst received a forensically sound copy of an employee's hard drive. The employee's manager
suspects inappropriate images may have been deleted from the hard drive. Which of the following could
help the analyst recover the deleted evidence?
suspects inappropriate images may have been deleted from the hard drive. Which of the following could
help the analyst recover the deleted evidence?
Question 153
A company invested ten percent of its entire annual budget in security technologies. The Chief Information Officer (CIO) is convinced that, without this investment, the company will risk being the next victim of the same cyber attack its competitor experienced three months ago. However, despite this investment, users are sharing their usernames and passwords with their coworkers to get their jobs done. Which of the following will eliminate the risk introduced by this practice?
Question 154
A security analyst is reviewing a report from the networking department that describes an increase in network utilization, which is causing network performance issues on some systems. A top talkers report over a five-minute sample is included.
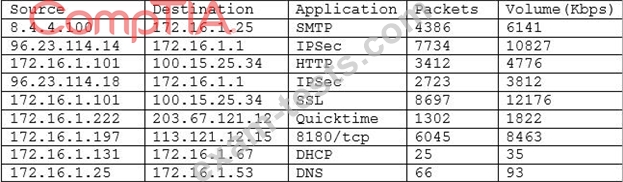
Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?

Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?
Question 155
SIMULATION
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS. If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean. If the vulnerability is valid, the analyst must remediate the finding. After reviewing the given information, select the STEP 2 tab in order to complete the simulation by selecting the correct "Validation Result" AND "Remediation Action" for each server listed using the drop down options.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
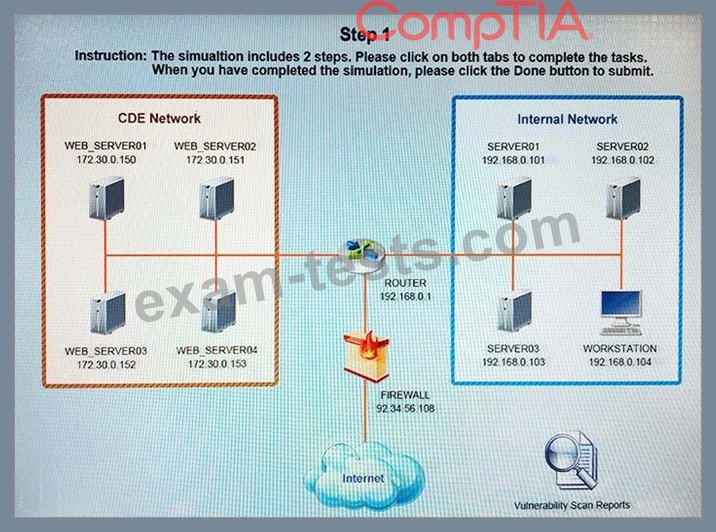
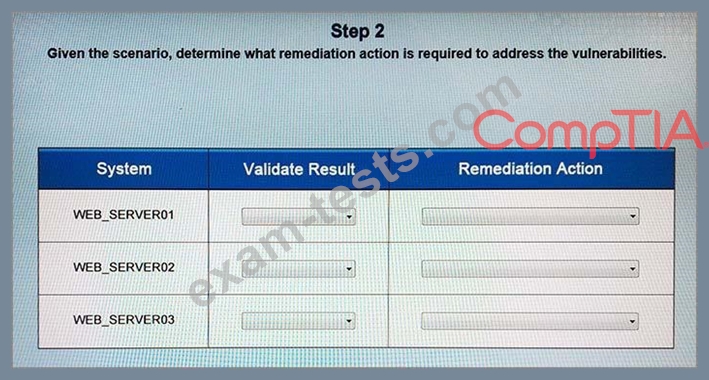
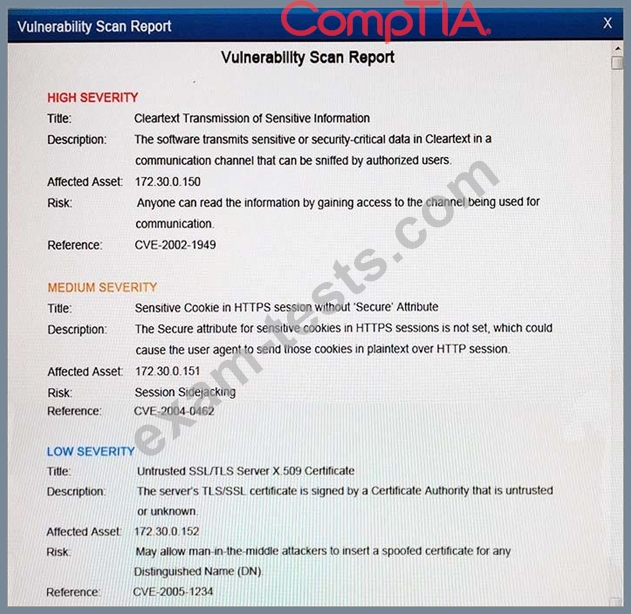
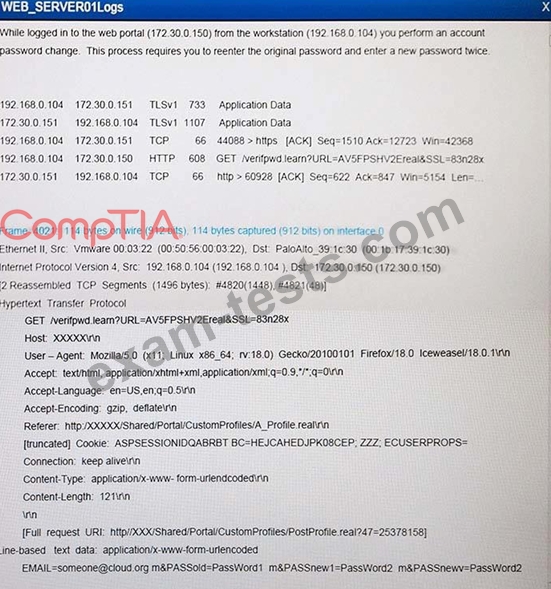
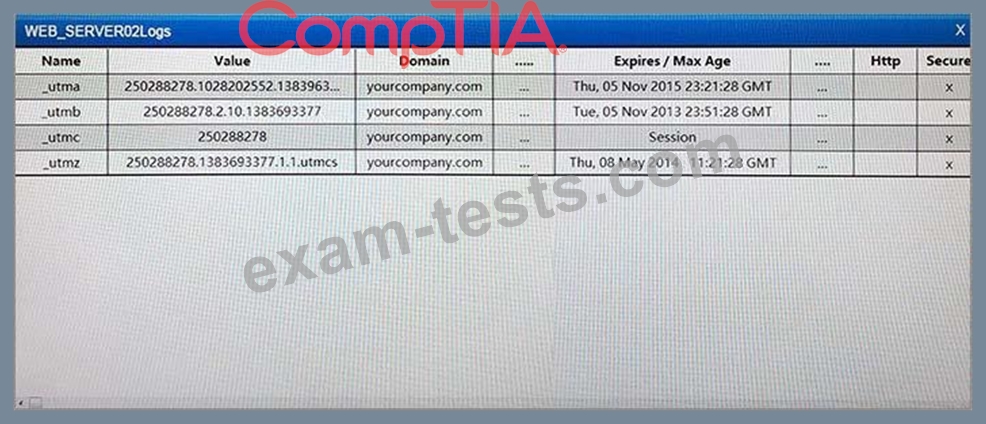
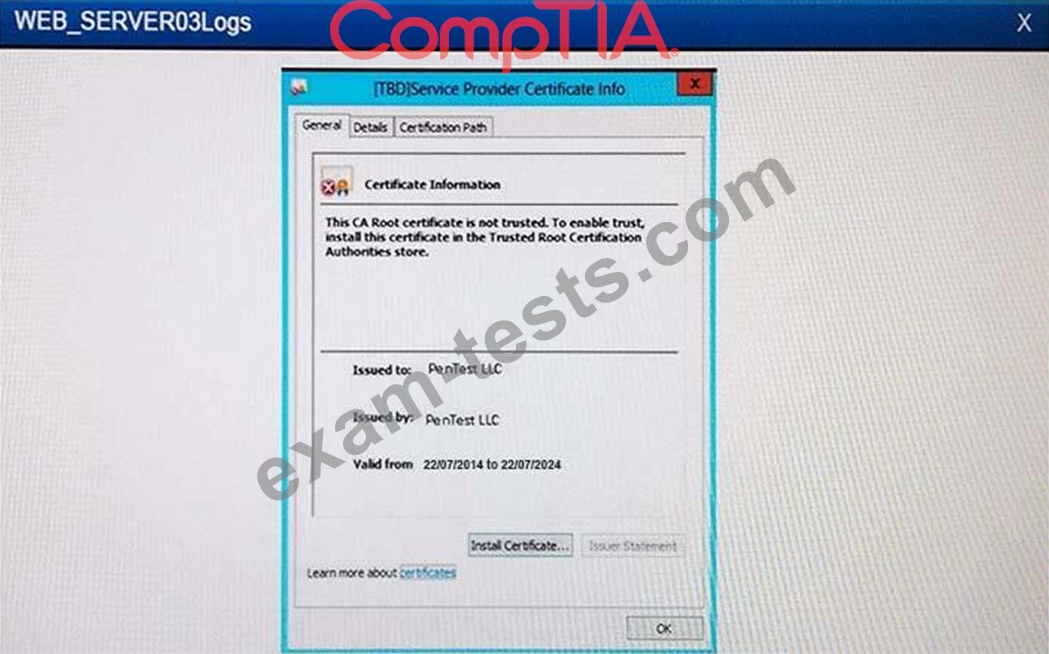
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS. If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean. If the vulnerability is valid, the analyst must remediate the finding. After reviewing the given information, select the STEP 2 tab in order to complete the simulation by selecting the correct "Validation Result" AND "Remediation Action" for each server listed using the drop down options.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.







