Question 161
In order to the leverage the power of data correlation with Nessus, a cybersecurity analyst must first be able to create a table for the scan results.
Given the following snippet of code:
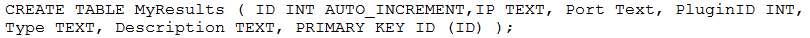
Which of the following output items would be correct?
Given the following snippet of code:
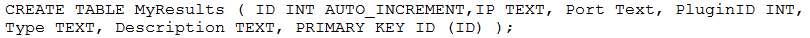
Which of the following output items would be correct?
Question 162
An investigation showed a worm was introduced from an engineer's laptop. It was determined the company does not provide engineers with company-owned laptops, which would be subject to company policy and technical controls.
Which of the following would be the MOST secure control implement?
Which of the following would be the MOST secure control implement?
Question 163
The following IDS log was discovered by a company's cybersecurity analyst:
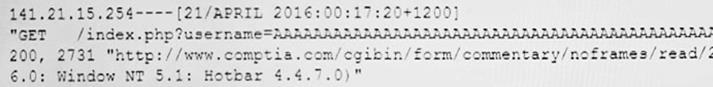
Which of the following was launched against the company based on the IDS log?

Which of the following was launched against the company based on the IDS log?
Question 164
A cybersecurity analyst is reviewing the following outputs:
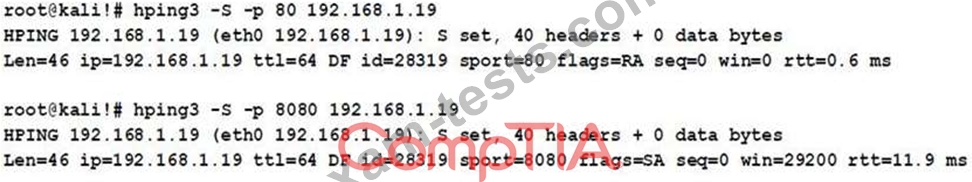
Which of the following can the analyst infer from the above output?

Which of the following can the analyst infer from the above output?
Question 165
The director of software development is concerned with recent web application security incidents, including the successful breach of a back-end database server. The director would like to work with the security team to implement a standardized way to design, build, and test web applications and the services that support them.
Which of the following meets the criteria?
Which of the following meets the criteria?

