Question 51
A pharmaceutical company's marketing team wants to send out notifications about new products to alert users of recalls and newly discovered adverse drug reactions. The team plans to use the names and mailing addresses that users have provided.
Which of the following data privacy standards does this violate?
Which of the following data privacy standards does this violate?
Question 52
An organization suspects it has had a breach, and it is trying to determine the potential impact. The organization knows the following:
* The source of the breach is linked to an IP located in a foreign country.
* The breach is isolated to the research and development servers.
* The hash values of the data before and after the breach are unchanged.
* The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
* The source of the breach is linked to an IP located in a foreign country.
* The breach is isolated to the research and development servers.
* The hash values of the data before and after the breach are unchanged.
* The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
Question 53
Which of the following software assessment methods would be BEST for gathering data related to an application's availability during peak times?
Question 54
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
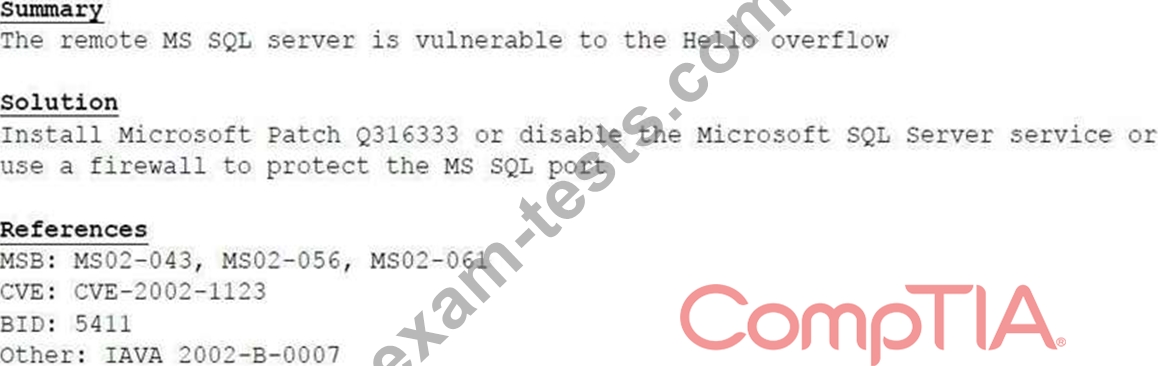
Based on the above information, which of the following should the system administrator do?
(Select TWO).

Based on the above information, which of the following should the system administrator do?
(Select TWO).
Question 55
A security analyst with an international response team is working to isolate a worldwide distribution of ransomware. The analyst is working with international governing bodies to distribute advanced intrusion detection routines for this variant of ransomware. Which of the following is the MOST important step with which the security analyst should comply?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

