Question 76
A cybersecurity analyst is currently auditing a new Active Directory server for compliance. The analyst uses Nessus to do the initial scan, and Nessus reports the following:
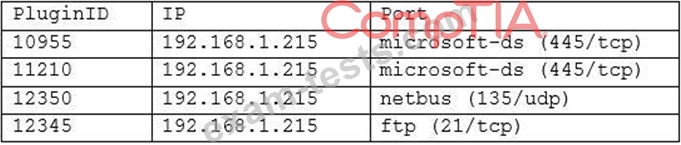
Which of the following critical vulnerabilities has the analyst discovered?

Which of the following critical vulnerabilities has the analyst discovered?
Question 77
A security analyst is reviewing the following log from an email security service.
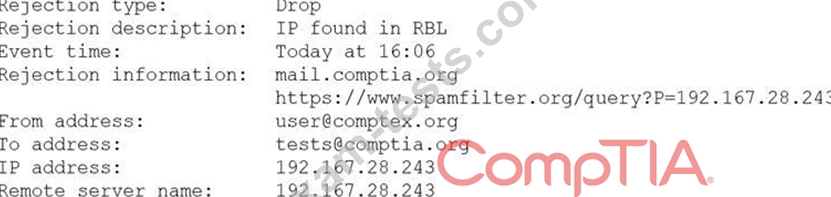
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 78
A security professional is analyzing the results of a network utilization report. The report includes the following information:
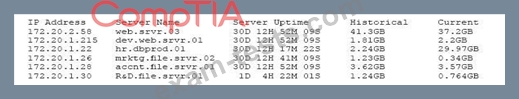
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?
Question 79
An analyst received a forensically sound copy of an employee's hard drive. The employee's manager suspects inappropriate images may have been deleted from the hard drive. Which of the following could help the analyst recover the deleted evidence?
Question 80
As part of an exercise set up by the information security officer, the IT staff must move some of the network systems to an off-site facility and redeploy them for testing. All staff members must ensure their respective systems can power back up and match their gold image. If they find any inconsistencies, they must formally document the information.
Which of the following BEST describes this test?
Which of the following BEST describes this test?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

