Question 86
A security analyst is investigating a malware infection that occurred on a Windows system.
The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage.
The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage.
The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
Question 87
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having outdated antivirus signatures. The analyst observes the following plugin output:
Antivirus is installed on the remote host:
Installation path: C:\Program Files\AVProduct\Win32\
Product Engine: 14.12.101
Engine Version: 3.5.71
Scanner does not currently have information about AVProduct version 3.5.71. It may no longer be supported.
The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor's website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
Antivirus is installed on the remote host:
Installation path: C:\Program Files\AVProduct\Win32\
Product Engine: 14.12.101
Engine Version: 3.5.71
Scanner does not currently have information about AVProduct version 3.5.71. It may no longer be supported.
The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor's website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
Question 88
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
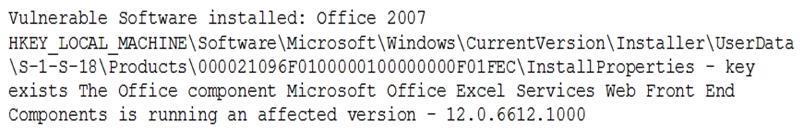
Which of the following actions should be taken?

Which of the following actions should be taken?
Question 89
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.
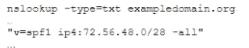
Given the output, which of the following should the security analyst check NEXT?

Given the output, which of the following should the security analyst check NEXT?
Question 90
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
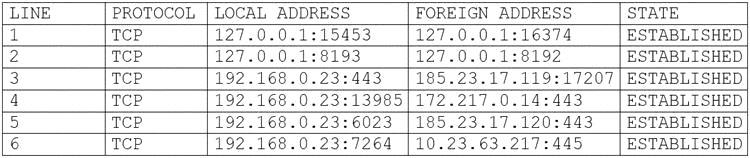
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

