Question 61
How many phases does the Spiral model cycle through?
Question 62
A company's asset management software has been discovering a weekly increase in non- standard software installed on end users' machines with duplicate license keys. The security analyst wants to know if any of this software is listening on any non-standard ports, such as 6667.
Which of the following tools should the analyst recommend to block any command and control traffic?
Which of the following tools should the analyst recommend to block any command and control traffic?
Question 63
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands:
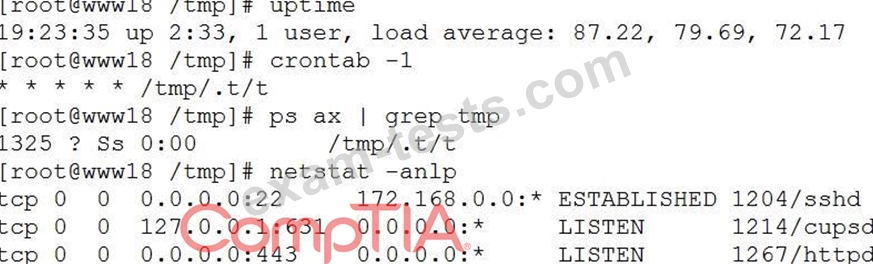
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Question 64
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period:

To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.

To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
Question 65
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently added to the existing ones. The analyst runs the following command on the new server.
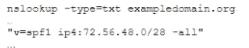
Given the output, which of the following should the security analyst check NEXT?

Given the output, which of the following should the security analyst check NEXT?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

