Question 96
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?


Question 97
A compliance officer of a large organization has reviewed the firm's vendor management program but has discovered there are no controls defined to evaluate third-party risk or hardware source authenticity. The compliance officer wants to gain some level of assurance on a recurring basis regarding the implementation of controls by third parties.
Which of the following would BEST satisfy the objectives defined by the compliance officer? (Choose two.)
Which of the following would BEST satisfy the objectives defined by the compliance officer? (Choose two.)
Question 98
Which of the following systems or services is MOST likely to exhibit issues stemming from the Heartbleed vulnerability (Choose two.)
Question 99
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancement to the company's cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
Question 100
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following:

The analyst runs the following command next:
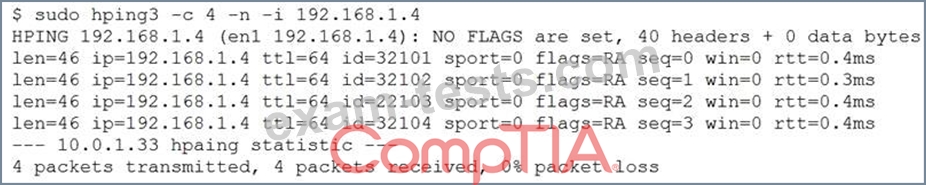
Which of the following would explain the difference in results?

The analyst runs the following command next:

Which of the following would explain the difference in results?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

