Question 116
A company's IDP/DLP solution triggered the following alerts:
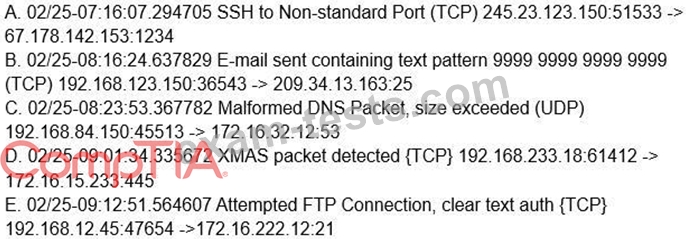
Which of the following alerts should a security analyst investigate FIRST?

Which of the following alerts should a security analyst investigate FIRST?
Question 117
A user receives a potentially malicious email that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review.
Which of the following commands would MOST likely indicate if the email is malicious?
Which of the following commands would MOST likely indicate if the email is malicious?
Question 118
A security analyst is reviewing the following log from an email security service.
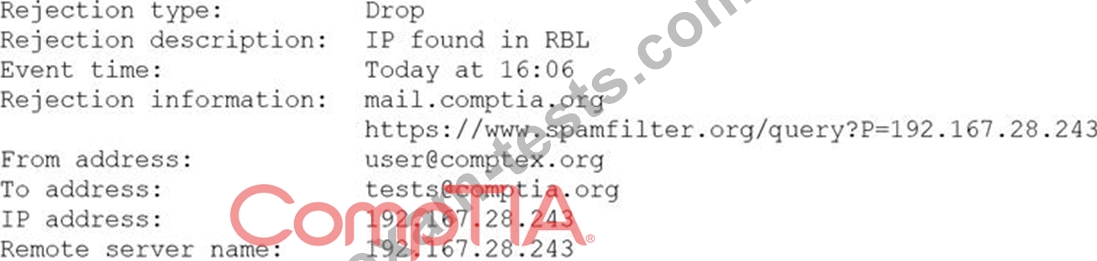
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 119
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets.
From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
Question 120
A security analyst reviews a recent network capture and notices encrypted inbound traffic on TCP port 465 was coming into the company's network from a database server. Which of the following will the security analyst MOST likely identify as the reason for the traffic on this port?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

