Question 131
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
Question 132
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
Question 133
A company's incident response team is handling a threat that was identified on the network. Security analysts have determined a web server is making multiple connections from TCP port 445 outbound to servers inside its subnet as well as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
Question 134
A company has established an ongoing vulnerability management program and procured the latest technology to support it. However, the program is failing because several vulnerabilities have not been detected. Which of the following will reduce the number of false negatives?
Question 135
A security analyst was alerted to a tile integrity monitoring event based on a change to the vhost-paymonts
.conf file The output of the diff command against the known-good backup reads as follows
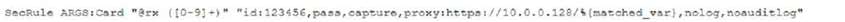
Which of the following MOST likely occurred?
.conf file The output of the diff command against the known-good backup reads as follows
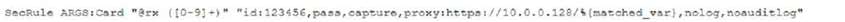
Which of the following MOST likely occurred?

