Question 126
A security analyst is providing a risk assessment for a medical device that will be installed on the corporate network. During the assessment, the analyst discovers the device has an embedded operating system that will be at the end of its life in two years. Due to the criticality of the device, the security committee makes a risk- based policy decision to review and enforce the vendor upgrade before the end of life is reached.
Which of the following risk actions has the security committee taken?
Which of the following risk actions has the security committee taken?
Question 127
An incident response report indicates a virus was introduced through a remote host that was connected to corporate resources.
A cybersecurity analyst has been asked for a recommendation to solve this issue.
Which of the following should be applied?
A cybersecurity analyst has been asked for a recommendation to solve this issue.
Which of the following should be applied?
Question 128
While reviewing a cyber-risk assessment, an analyst notes there are concerns related to FPGA usage. Which of the following statements would BEST convince the analyst's supervisor to use additional controls?
Question 129
Understanding attack vectors and integrating intelligence sources are important components of:
Question 130
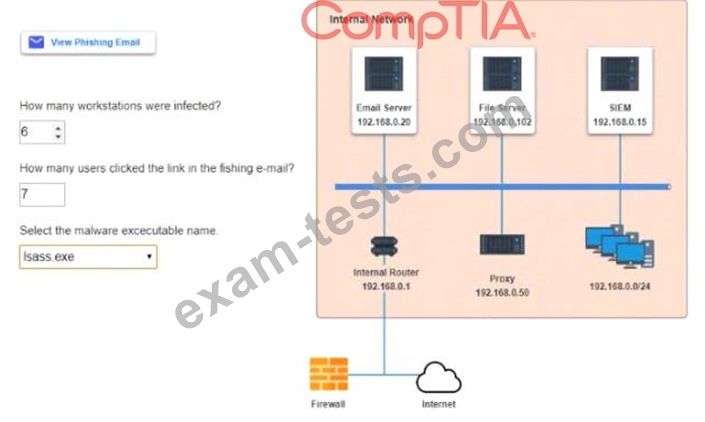
Approximately 100 employees at your company have received a phishing email. As a security analyst you have been tasked with handling this situation.
INSTRUCTIONS
Review the information provided and determine the following:
1. How many employees clicked on the link in the phishing email?
2. On how many workstations was the malware installed?
3. What is the executable file name or the malware?
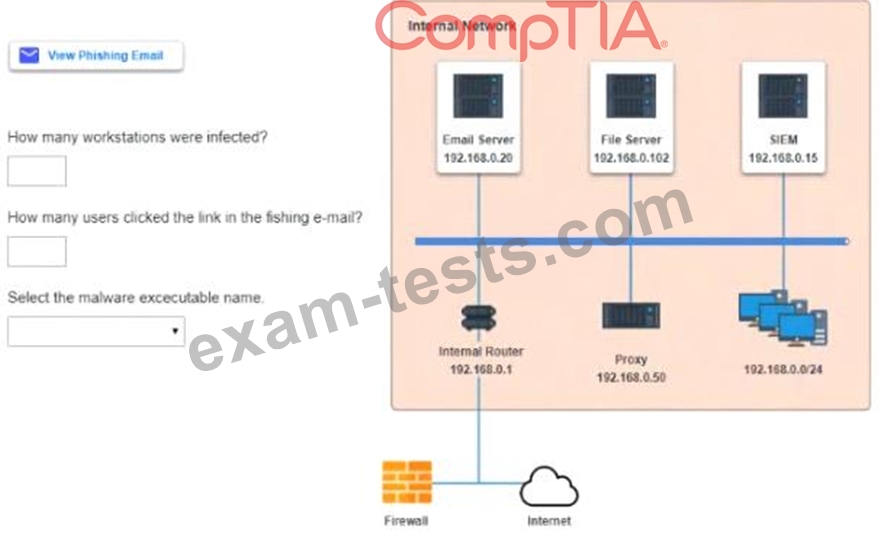
INSTRUCTIONS
Review the information provided and determine the following:
1. How many employees clicked on the link in the phishing email?
2. On how many workstations was the malware installed?
3. What is the executable file name or the malware?