Question 136
Employees at a manufacturing plant have been victims of spear phishing, but security solutions prevented further intrusions into the network. Which of the following is the MOST appropriate solution in this scenario?
Question 137
A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities The type of vulnerability that should be disseminated FIRST is one that:
Question 138
A security analyst is reviewing IDS logs and notices the following entry:

Which of the following attacks is occurring?

Which of the following attacks is occurring?
Question 139
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session.
Which of the following is the BEST technique to address the CISO's concerns?
Which of the following is the BEST technique to address the CISO's concerns?
Question 140
Given the following access log:
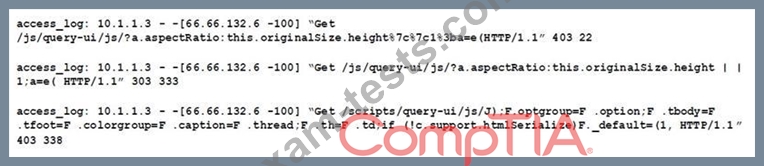
Which of the following accurately describes what this log displays?

Which of the following accurately describes what this log displays?

