Question 206
A security analyst is conducting traffic analysis and observes an HTTP POST to a web server.
The POST header is approximately 1000 bytes in length. During transmission, one byte is delivered every ten seconds. Which of the following attacks is the traffic indicative of?
The POST header is approximately 1000 bytes in length. During transmission, one byte is delivered every ten seconds. Which of the following attacks is the traffic indicative of?
Question 207
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users.
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
* Locky.js
* xerty.ini
* xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
* Locky.js
* xerty.ini
* xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
Question 208
An application contains the following log entries in a file named "authlog.log":

A security analyst has been asked to parse the log file and print out all valid usernames. Which of the following achieves this task?

A security analyst has been asked to parse the log file and print out all valid usernames. Which of the following achieves this task?
Question 209
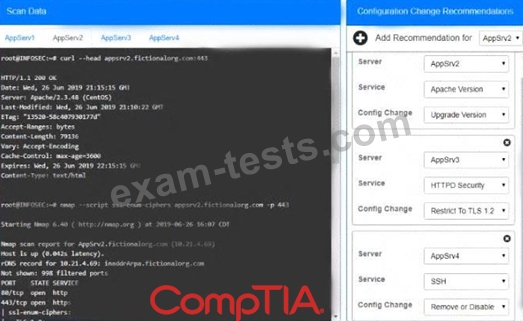
You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers. You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following:
* TLS 1.2 is the only version of TLS running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.
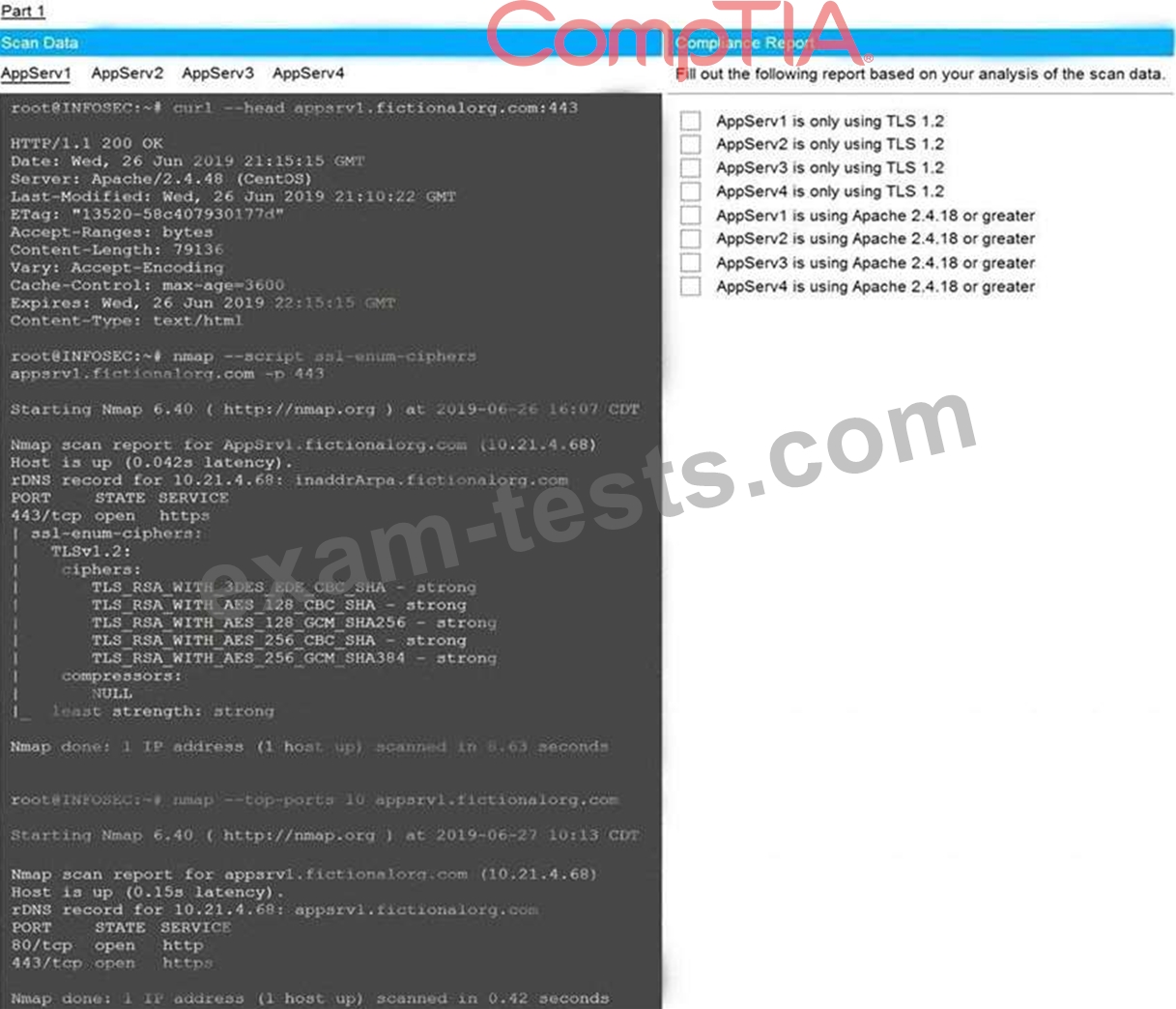
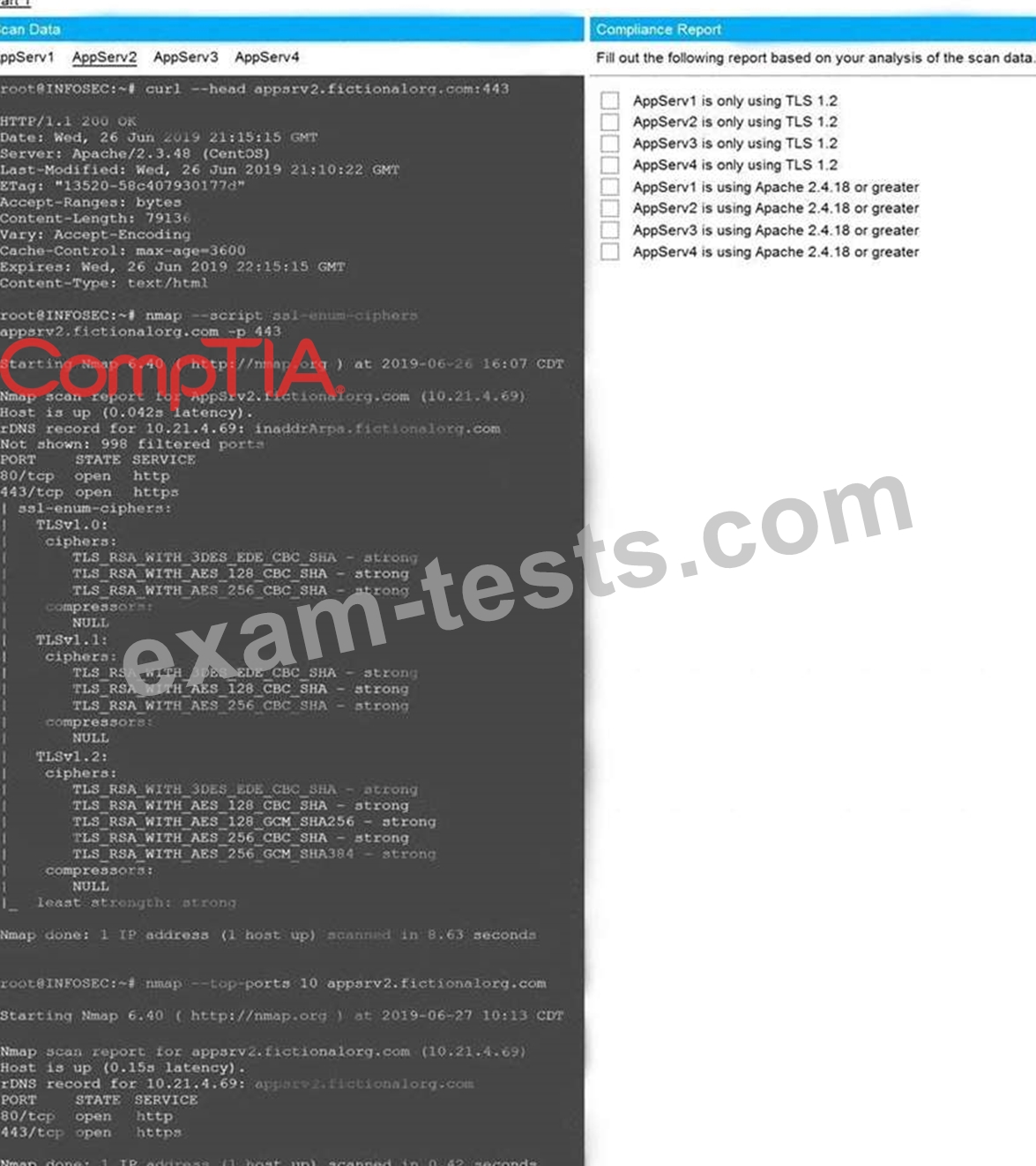
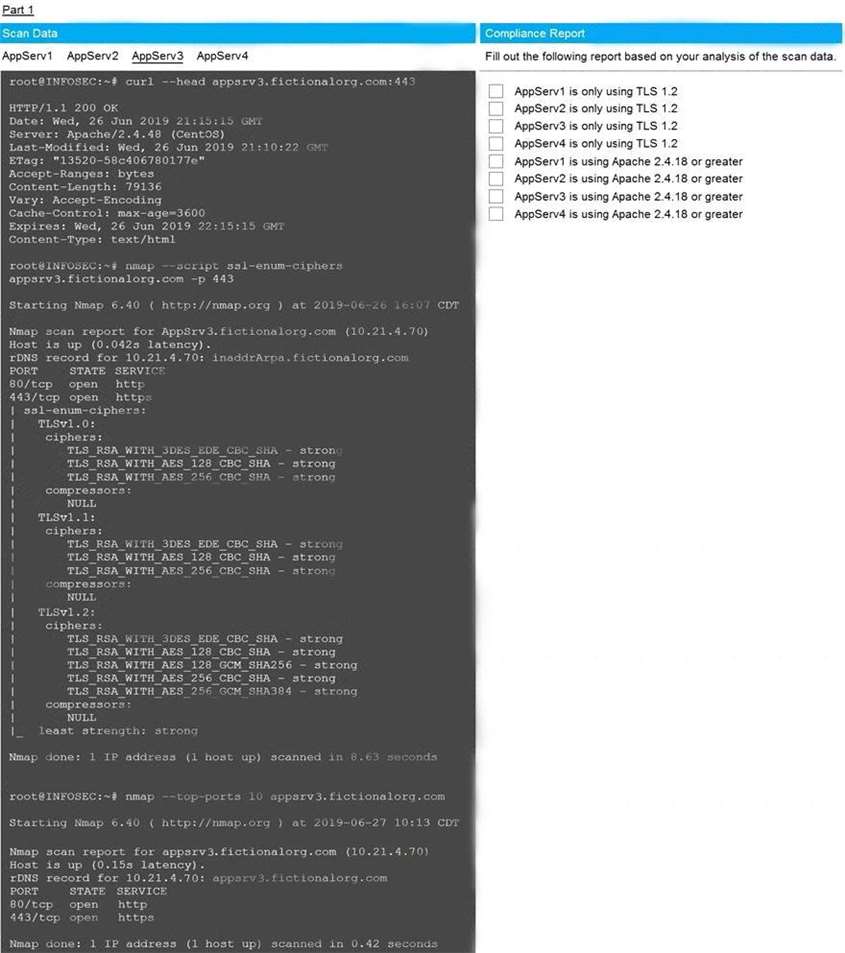
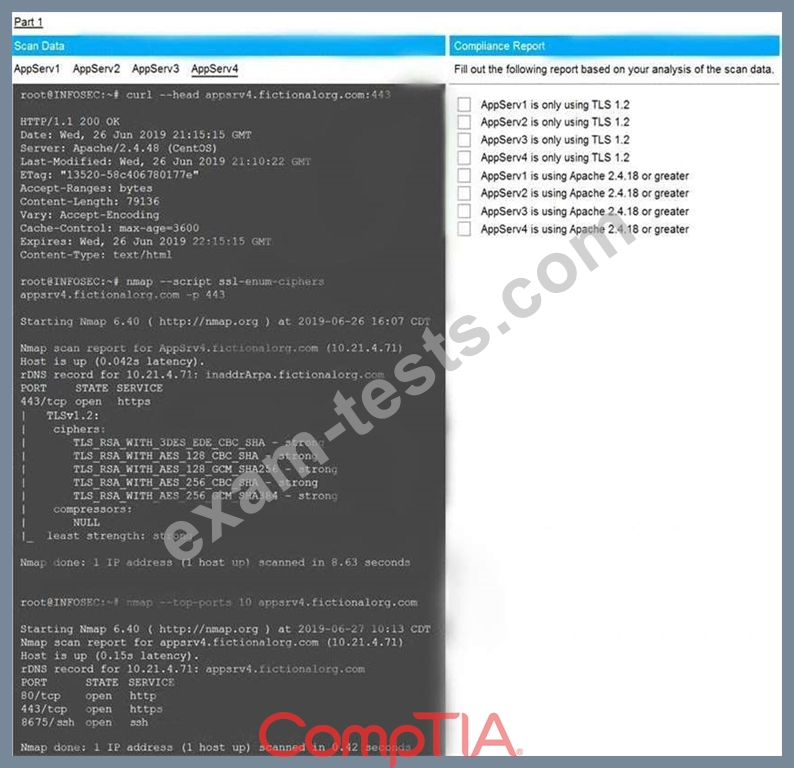

The company's hardening guidelines indicate the following:
* TLS 1.2 is the only version of TLS running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based ONLY on the hardening guidelines provided.





Question 210
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
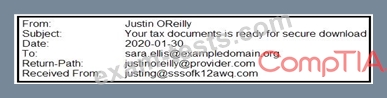
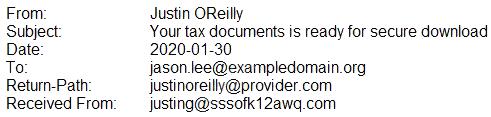
Which of the following technologies would MOST likely be used to prevent this phishing attempt?


Which of the following technologies would MOST likely be used to prevent this phishing attempt?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here: