Question 196
Due to a security breach initiated from South America, the Chief Security Officer (CSO) instructed a team to design and implement an appropriate security control to prevent such an attack from reoccurring. The company has sales and consulting teams across the United States that need access to company resources. The security manager implemented a location-based authentication to prevent non-US-based access to the company networks. Three months later, the same incident reoccurred with an attack originating from a country in Asia. Which of the following security design defects could be the cause?
Question 197
Which of the following are essential components within the rules of engagement for a penetration test? (Select TWO).
Question 198
A security analyst is investigating an incident that appears to have started with SOL injection against a publicly available web application. Which of the following is the FIRST step the analyst should take to prevent future attacks?
Question 199
A system's authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now. The cybersecurity group just performed a vulnerability scan with the partial set of results shown below:
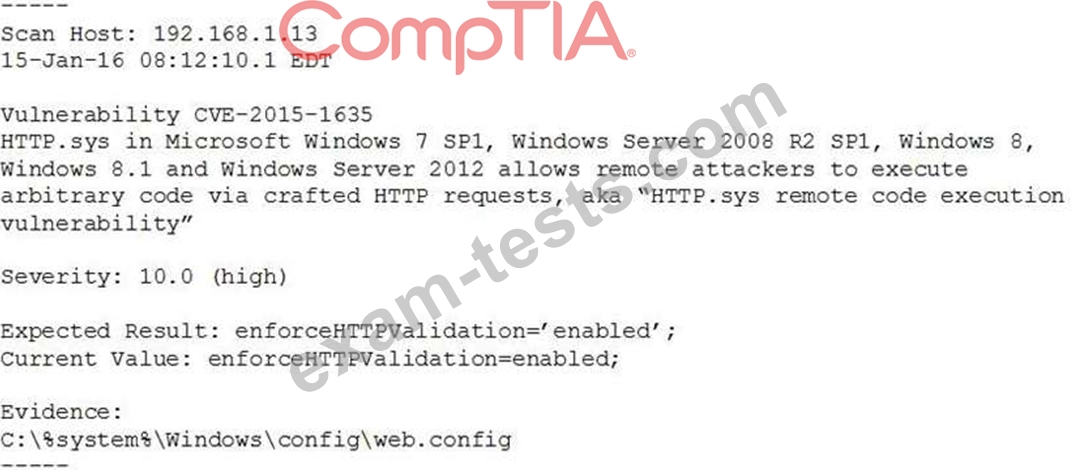
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?

Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
Question 200
An organization is experiencing issues with emails that are being sent to external recipients Incoming emails to the organization are working fine. A security analyst receives the following screenshot ot email error from the help desk.

The analyst the checks the email server and sees many of the following messages in the logs.
Error 550 - Message rejected
Which of the following is MOST likely the issue?

The analyst the checks the email server and sees many of the following messages in the logs.
Error 550 - Message rejected
Which of the following is MOST likely the issue?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

