Question 216
Which of the following should be found within an organization's acceptable use policy?
Question 217
A storage area network (SAN) was inadvertently powered off while power maintenance was being performed in a datacenter. None of the systems should have lost all power during the maintenance. Upon review, it is discovered that a SAN administrator moved a power plug when testing the SAN's fault notification features.
Which of the following should be done to prevent this issue from reoccurring?
Which of the following should be done to prevent this issue from reoccurring?
Question 218
A security analyst is preparing for the company's upcoming audit. Upon review of the company's latest vulnerability scan, the security analyst finds the following open issues:
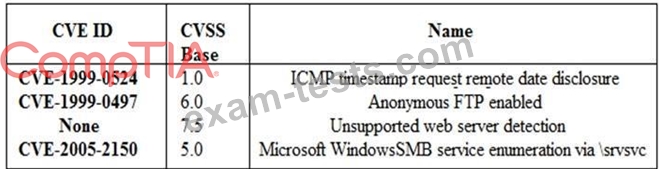
Which of the following vulnerabilities should be prioritized for remediation FIRST?

Which of the following vulnerabilities should be prioritized for remediation FIRST?
Question 219
While analyzing logs from a WAF, a cybersecurity analyst finds the following:
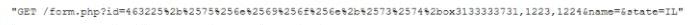
Which of the following BEST describes what the analyst has found?
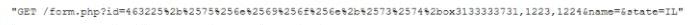
Which of the following BEST describes what the analyst has found?
Question 220
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session. Which of the following is the BEST technique to address the CISO's concerns?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

