Question 1
The security analyst received the monthly vulnerability report. The following findings were included in the report
* Five of the systems only required a reboot to finalize the patch application.
* Two of the servers are running outdated operating systems and cannot be patched The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them.
Which of the following approaches will best minimize the risk of the outdated servers being compromised?
* Five of the systems only required a reboot to finalize the patch application.
* Two of the servers are running outdated operating systems and cannot be patched The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them.
Which of the following approaches will best minimize the risk of the outdated servers being compromised?
Question 2
A cybersecurity analyst notices unusual network scanning activity coming from a country that the company does not do business with. Which of the following is the best mitigation technique?
Question 3
Which of the following describes how a CSIRT lead determines who should be communicated with and when during a security incident?
Question 4
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:
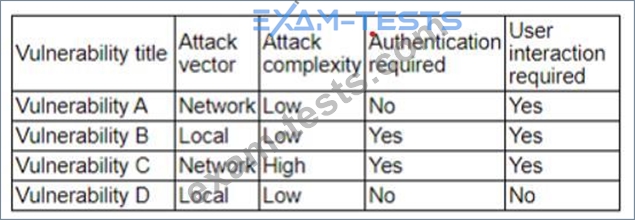
Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?

Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
Question 5
Which of the following describes the best reason for conducting a root cause analysis?

