Question 81
An organization's email account was compromised by a bad actor. Given the following information:
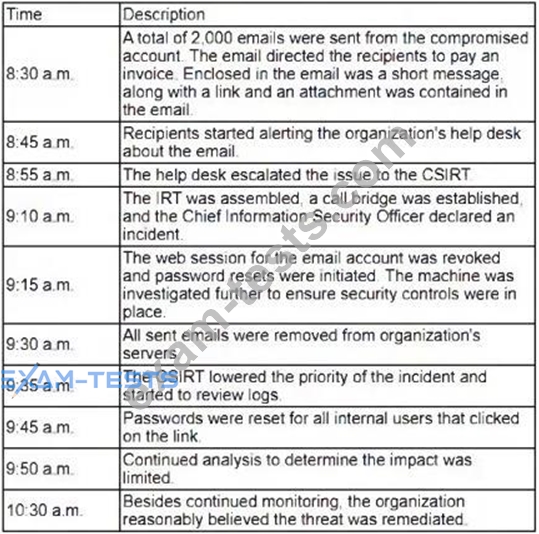
Which of the following is the length of time the team took to detect the threat?

Which of the following is the length of time the team took to detect the threat?
Question 82
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
Question 83
A security analyst is investigating an unusually high volume of requests received on a web server. Based on the following command and output:
access_log - [21/May/2024 13:19:06] "GET /newyddion HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /1970 HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /dopey HTTP/1.1" 404 -
...
Which of the following best describes the activity that the analyst will confirm?
access_log - [21/May/2024 13:19:06] "GET /newyddion HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /1970 HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /dopey HTTP/1.1" 404 -
...
Which of the following best describes the activity that the analyst will confirm?
Question 84
A cloud team received an alert that unauthorized resources were being auto-provisioned. After investigating, the team suspects that crypto mining is occurring. Which of the following indicators would most likely lead the team to this conclusion?
.
.
Question 85
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts The company's AUP and code of conduct prohibits this practice. Which of the following configuration changes would improve security and help prevent this from occurring?

