Question 101
A security administrator has found indications of dictionary attacks against the company's external- facing portal. Which of the following should be implemented to best mitigate the password attacks?
Question 102
During an incident involving phishing, a security analyst needs to find the source of the malicious email. Which of the following techniques would provide the analyst with this information?
Question 103
An employee is no longer able to log in to an account after updating a browser. The employee usually has several tabs open in the browser. Which of the following attacks was most likely performed?
Question 104
A company brings in a consultant to make improvements to its website. After the consultant leaves. a web developer notices unusual activity on the website and submits a suspicious file containing the following code to the security team:
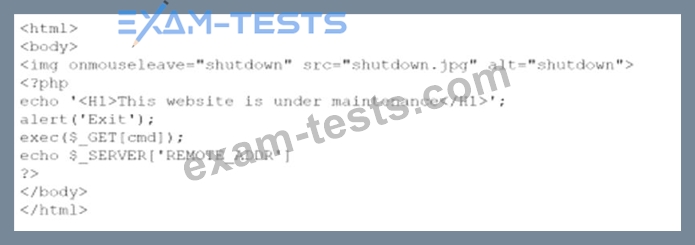
Which of the following did the consultant do?

Which of the following did the consultant do?
Question 105
ID
Source
Destination
Protocol
Service
1
172.16.1.1
172.16.1.10
ARP
AddrResolve
2
172.16.1.10
172.16.1.20
TCP 135
RPC Kerberos
3
172.16.1.10
172.16.1.30
TCP 445
SMB WindowsExplorer
4
172.16.1.30
5.29.1.5
TCP 443
HTTPS Browser.exe
5
11.4.11.28
172.16.1.1
TCP 53
DNS Unknown
6
20.109.209.108
172.16.1.1
TCP 443
HTTPS WUS
7
172.16.1.25
bank.backup.com
TCP 21
FTP FileZilla
Which of the following represents the greatest concerns with regard to potential data exfiltration? (Select two.)
Source
Destination
Protocol
Service
1
172.16.1.1
172.16.1.10
ARP
AddrResolve
2
172.16.1.10
172.16.1.20
TCP 135
RPC Kerberos
3
172.16.1.10
172.16.1.30
TCP 445
SMB WindowsExplorer
4
172.16.1.30
5.29.1.5
TCP 443
HTTPS Browser.exe
5
11.4.11.28
172.16.1.1
TCP 53
DNS Unknown
6
20.109.209.108
172.16.1.1
TCP 443
HTTPS WUS
7
172.16.1.25
bank.backup.com
TCP 21
FTP FileZilla
Which of the following represents the greatest concerns with regard to potential data exfiltration? (Select two.)

