Question 91
Which of the following best describes the key goal of the containment stage of an incident response process?
Question 92
A security audit for unsecured network services was conducted, and the following output was generated:
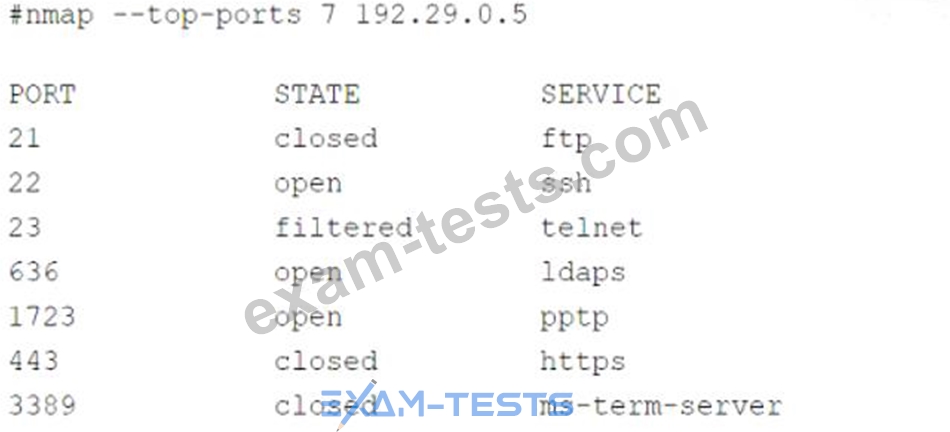
Which of the following services should the security team investigate further? (Select two).

Which of the following services should the security team investigate further? (Select two).
Question 93
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
Question 94
Executives at an organization email sensitive financial information to external business partners when negotiating valuable contracts. To ensure the legal validity of these messages, the cybersecurity team recommends a digital signature be added to emails sent by the executives.
Which of the following are the primary goals of this recommendation? (Choose two.)
Which of the following are the primary goals of this recommendation? (Choose two.)
Question 95
A security learn implemented a SCM as part for its security-monitoring program there is a requirement to integrate a number of sources Into the SIEM to provide better context relative to the events being processed. Which of the following BST describes the result the security learn hopes to accomplish by adding these sources?

