Question 86
An organization utilizes multiple vendors, each with its own portal that a security analyst must sign in to daily. Which of the following is the best solution for the organization to use to eliminate the need for multiple authentication credentials?
Question 87
Hotspot Question
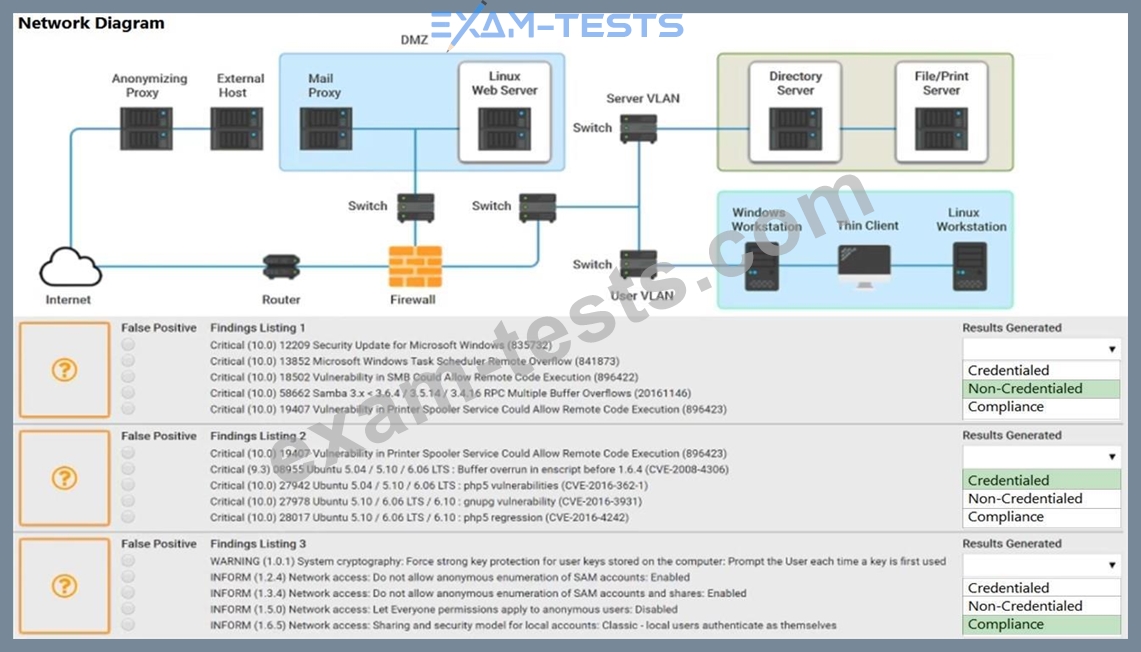
A security analyst performs various types of vulnerability scans. You must review the vulnerability scan results to determine the type of scan that was executed and determine if a false positive occurred for each device.
Instructions:
Select the drop option for whether the results were generated from a credentialed scan, non- credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives.
NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.
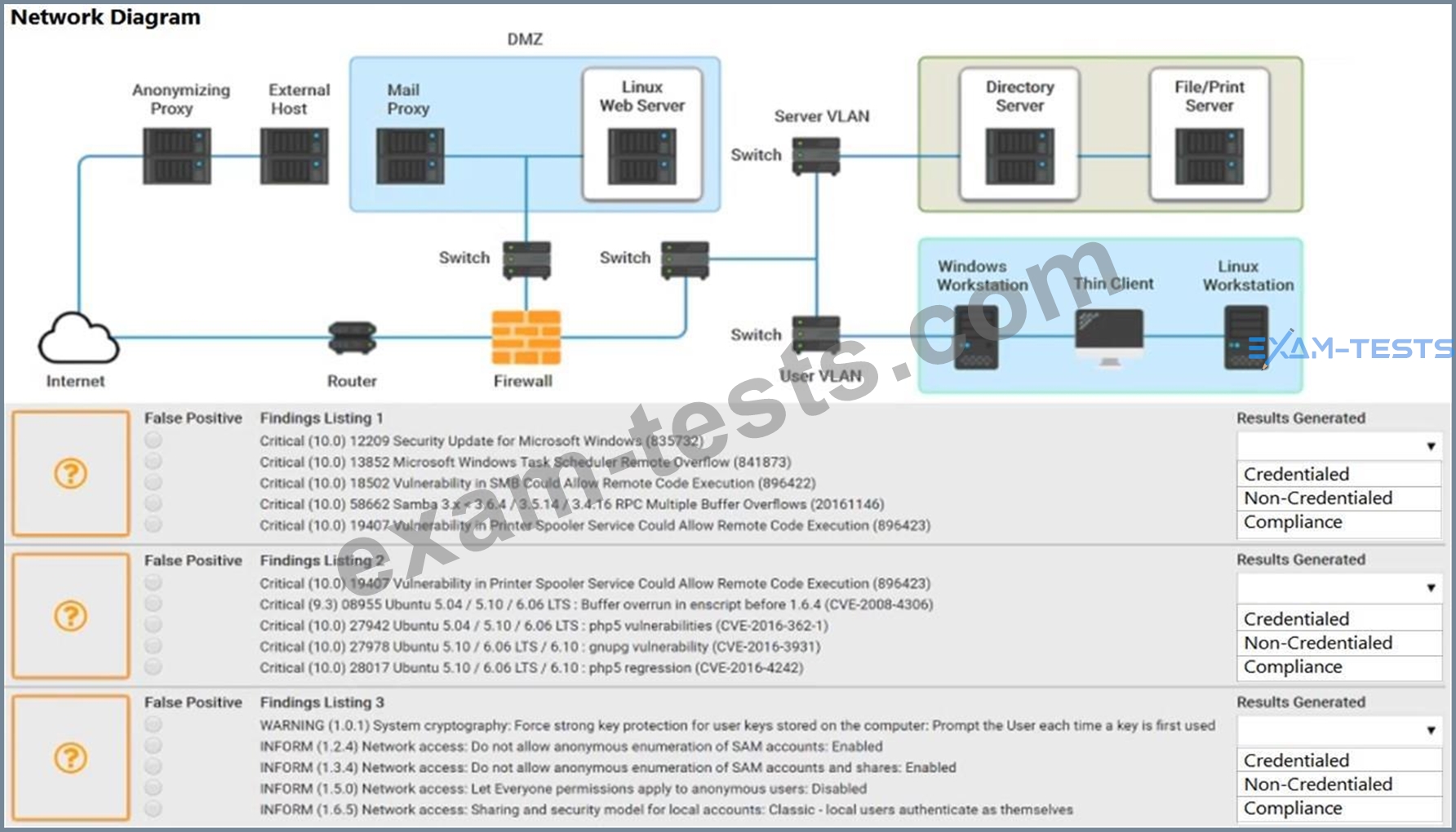
A security analyst performs various types of vulnerability scans. You must review the vulnerability scan results to determine the type of scan that was executed and determine if a false positive occurred for each device.
Instructions:
Select the drop option for whether the results were generated from a credentialed scan, non- credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives.
NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.

Question 88
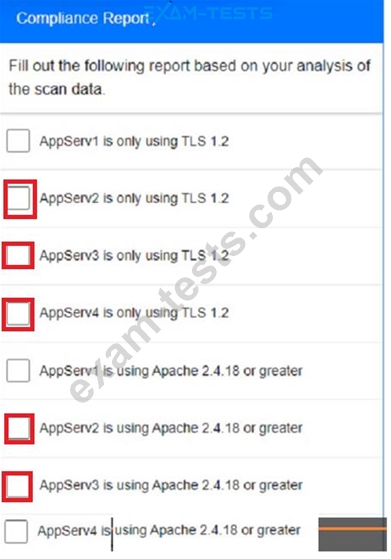
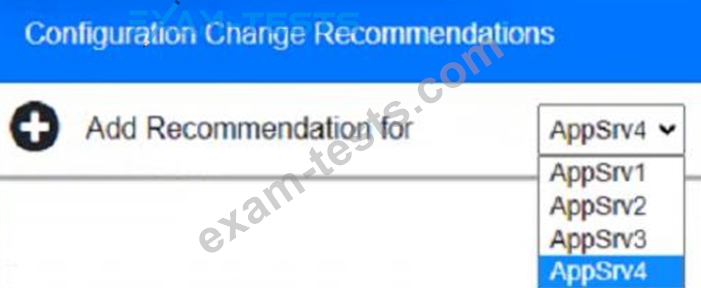
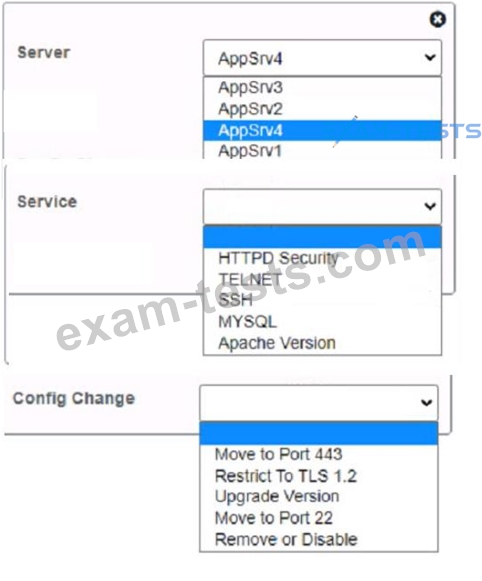
You are a cybersecurity analyst tasked with interpreting scan data from Company As servers You must verify the requirements are being met for all of the servers and recommend changes if you find they are not The company's hardening guidelines indicate the following
* TLS 1 2 is the only version of TLS
running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
using the supplied dat
a. record the status of compliance With the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for Issues based ONLY on the hardening guidelines provided.
Part 1:
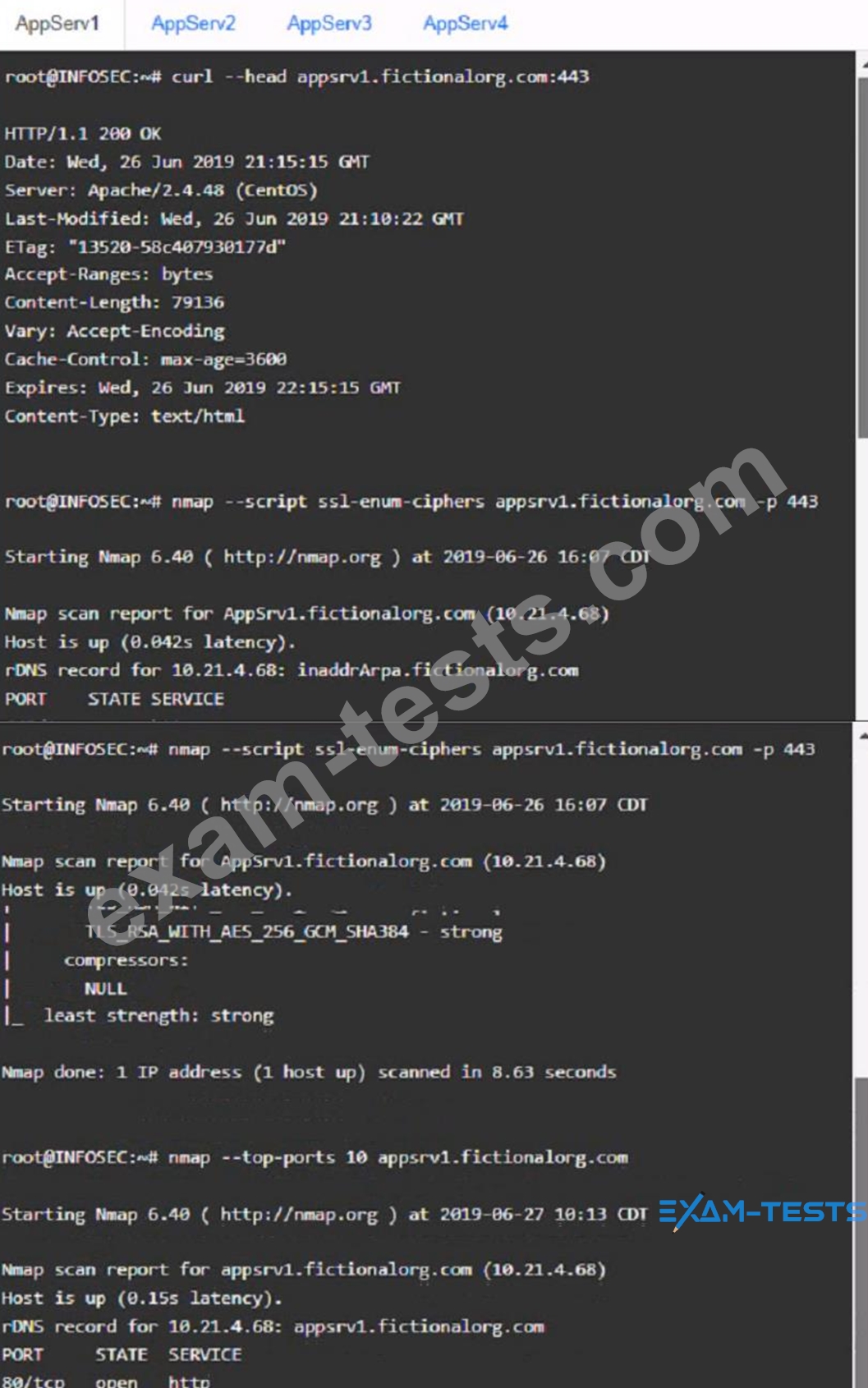
AppServ2:
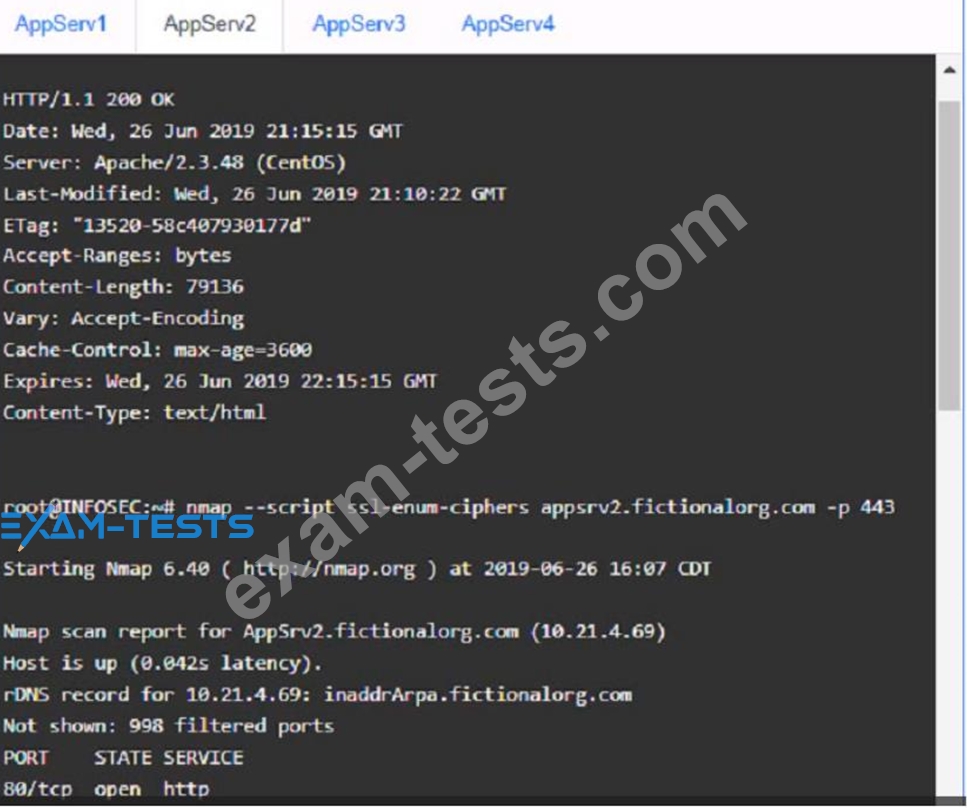
AppServ3:
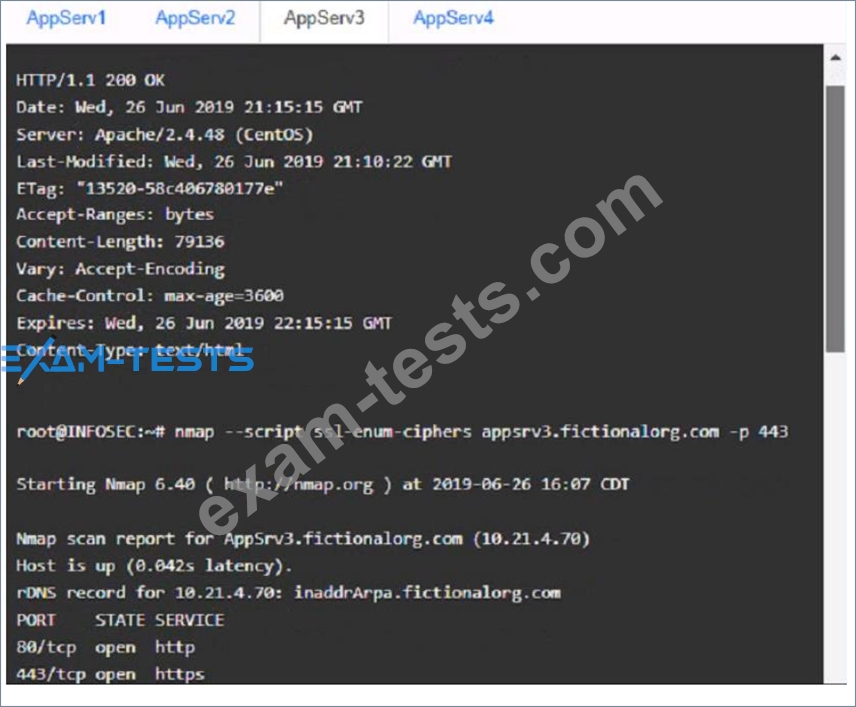
AppServ4:
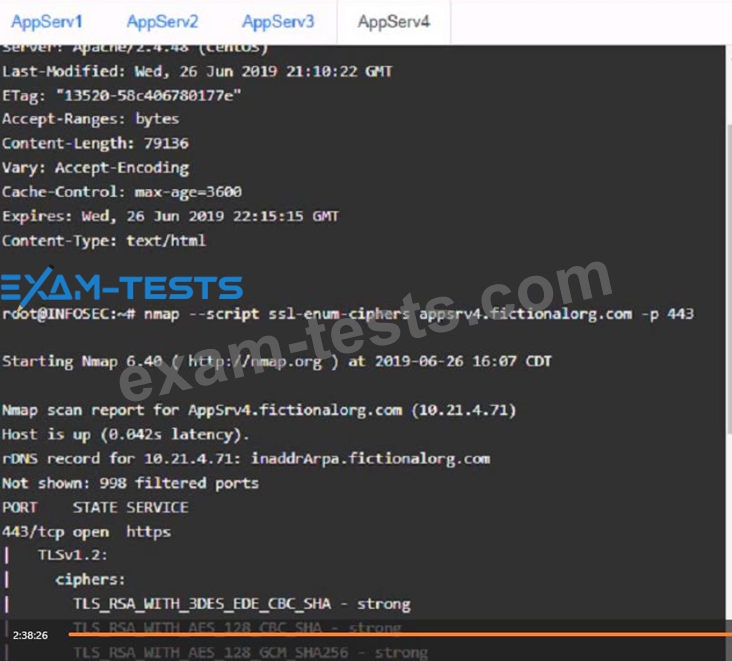
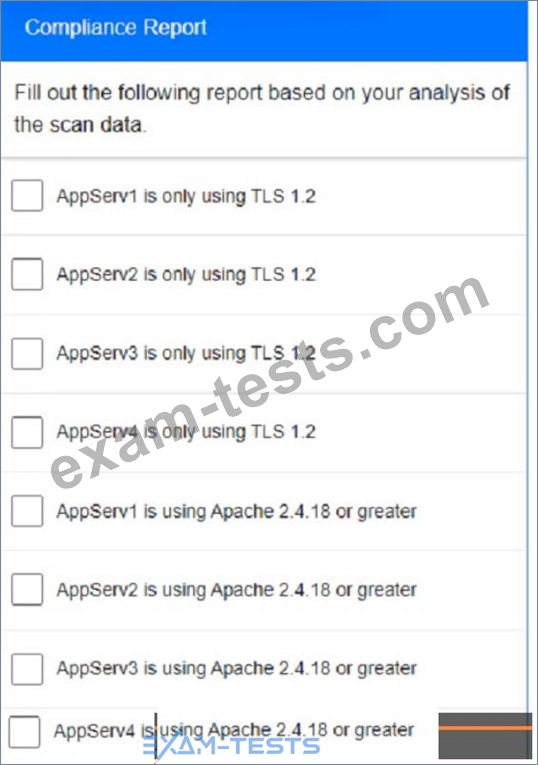
Part 2:
* TLS 1 2 is the only version of TLS
running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
using the supplied dat
a. record the status of compliance With the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for Issues based ONLY on the hardening guidelines provided.
Part 1:

AppServ2:

AppServ3:

AppServ4:


Part 2:


Question 89
A company classifies security groups by risk level. Any group with a high-risk classification requires multiple levels of approval for member or owner changes. Which of the following inhibitors to remediation is the company utilizing?
Question 90
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?