Question 106
An attacker recently gained unauthorized access to a financial institution's database, which contains confidential information. The attacker exfiltrated a large amount of data before being detected and blocked. A security analyst needs to complete a root cause analysis to determine how the attacker was able to gain access. Which of the following should the analyst perform first?
Question 107
Using open-source intelligence gathered from technical forums, a threat actor compiles and tests a malicious downloader to ensure it will not be detected by the victim organization's endpoint security protections. Which of the following stages of the Cyber Kill Chain best aligns with the threat actor's actions?
Question 108
Which of the following makes STIX and OpenloC information readable by both humans and machines?
Question 109
A security analyst receives an alert for suspicious activity on a company laptop An excerpt of the log is shown below:
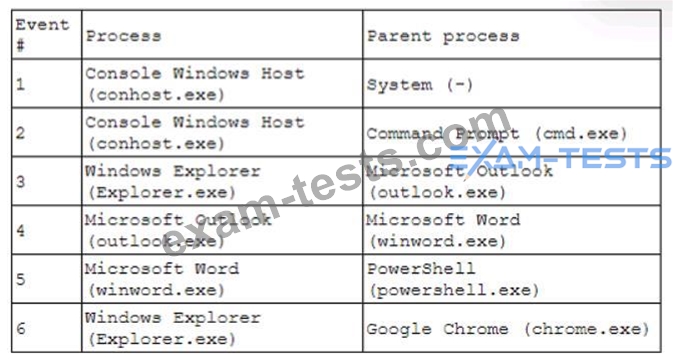
Which of the following has most likely occurred?

Which of the following has most likely occurred?
Question 110
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?

