Question 121
A Chief Information Security Officer (CISO) is concerned that a specific threat actor who is known to target the company's business type may be able to breach the network and remain inside of it for an extended period of time.
Which of the following techniques should be performed to meet the CISO's goals?
Which of the following techniques should be performed to meet the CISO's goals?
Question 122
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:

Follow TCP stream:
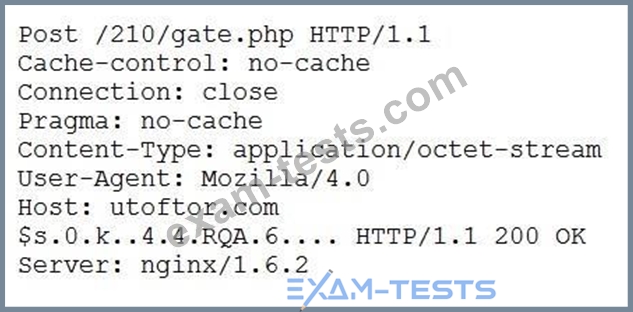
Which of the following describes what has occurred?

Follow TCP stream:

Which of the following describes what has occurred?
Question 123
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
Question 124
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
Which of the following metrics should the team lead include in the briefs?
Question 125
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?

