Question 111
After an upgrade to a new EDR, a security analyst received reports that several endpoints were not communicating with the SaaS provider to receive critical threat signatures. To comply with the incident response playbook, the security analyst was required to validate connectivity to ensure communications. The security analyst ran a command that provided the following output:
ComputerName: comptia007
RemotePort: 443
InterfaceAlias: Ethernet 3
TcpTestSucceeded: False
Which of the following did the analyst use to ensure connectivity?
ComputerName: comptia007
RemotePort: 443
InterfaceAlias: Ethernet 3
TcpTestSucceeded: False
Which of the following did the analyst use to ensure connectivity?
Question 112
A security analyst is trying to detect connections to a suspicious IP address by collecting the packet captures from the gateway. Which of the following commands should the security analyst consider running?
Question 113
A user reports a message as suspicious to the IT security team. An analyst reviews the message and notices that the following text string becomes a hyperlink in an email:
%77%77%77%2e%69%63%65%2d%70%74%69%63%2e%63%6f%6d
Which of the following would most likely explain this behavior?
%77%77%77%2e%69%63%65%2d%70%74%69%63%2e%63%6f%6d
Which of the following would most likely explain this behavior?
Question 114
A company recently removed administrator rights from all of its end user workstations. An analyst uses CVSSv3.1 exploitability metrics to prioritize the vulnerabilities for the workstations and produces the following information:
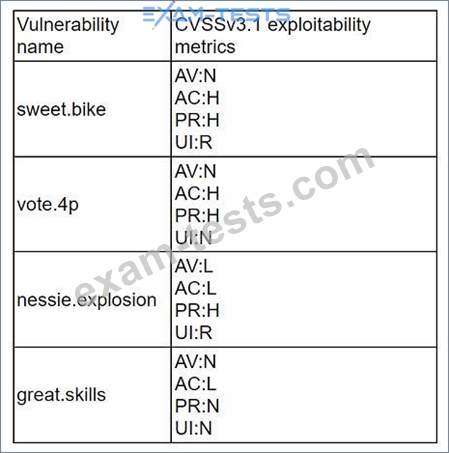
Which of the following vulnerabilities should be prioritized for remediation?

Which of the following vulnerabilities should be prioritized for remediation?
Question 115
An organization identifies a method to detect unexpected behavior, crashes, or resource leaks in a system by feeding invalid, unexpected, or random data to stress the application. Which of the following best describes this testing methodology?

