Question 66
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
Question 67
Click the exhibit button.
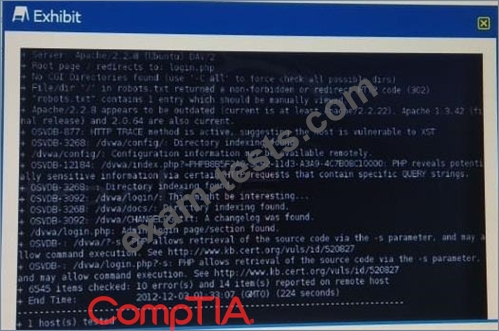
Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)

Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)
Question 68
A manager calls upon a tester to assist with diagnosing an issue within the following Python script:
#!/usr/bin/python
s = "Administrator"
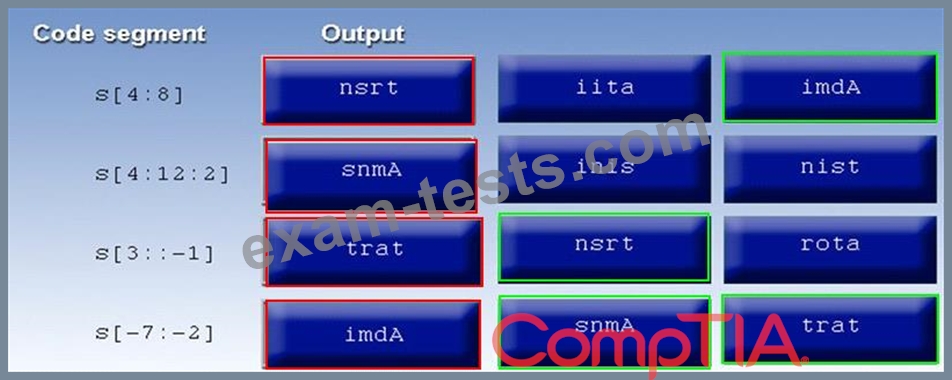
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment Options may be used once or not at all

#!/usr/bin/python
s = "Administrator"
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment Options may be used once or not at all

Question 69
A company requested a penetration tester review the security of an in-house-developed Android application.
The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST?
(Select TWO)
The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST?
(Select TWO)
Question 70
Click the exhibit button.
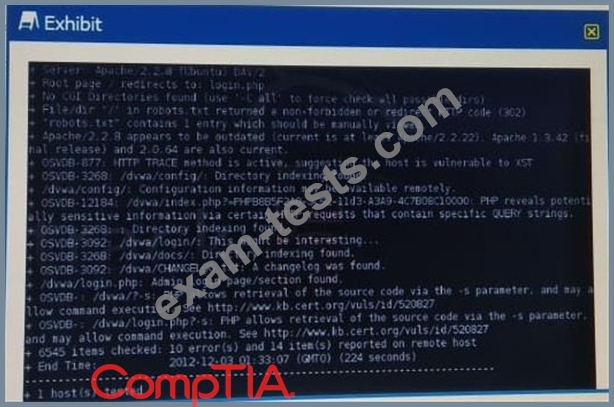
Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)

Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)