Question 61
Which of the following tools is used to perform a credential brute force attack?
Question 62
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once


Question 63
Given the following script:
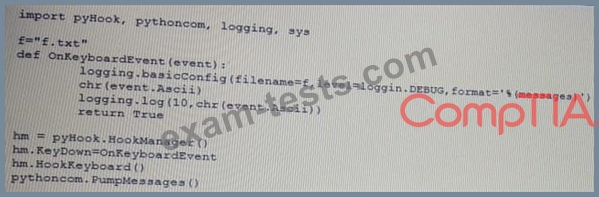
Which of the following BEST describes the purpose of this script?

Which of the following BEST describes the purpose of this script?
Question 64
A penetration tester is perform initial intelligence gathering on some remote hosts prior to conducting a vulnerability < The tester runs the following command nmap -D 192.168.1.1,192.168.1.2,192.168.1.3 -sV -o -max rate 2 192. 168.130 Which ol the following BEST describes why multiple IP addresses are specified?
Question 65
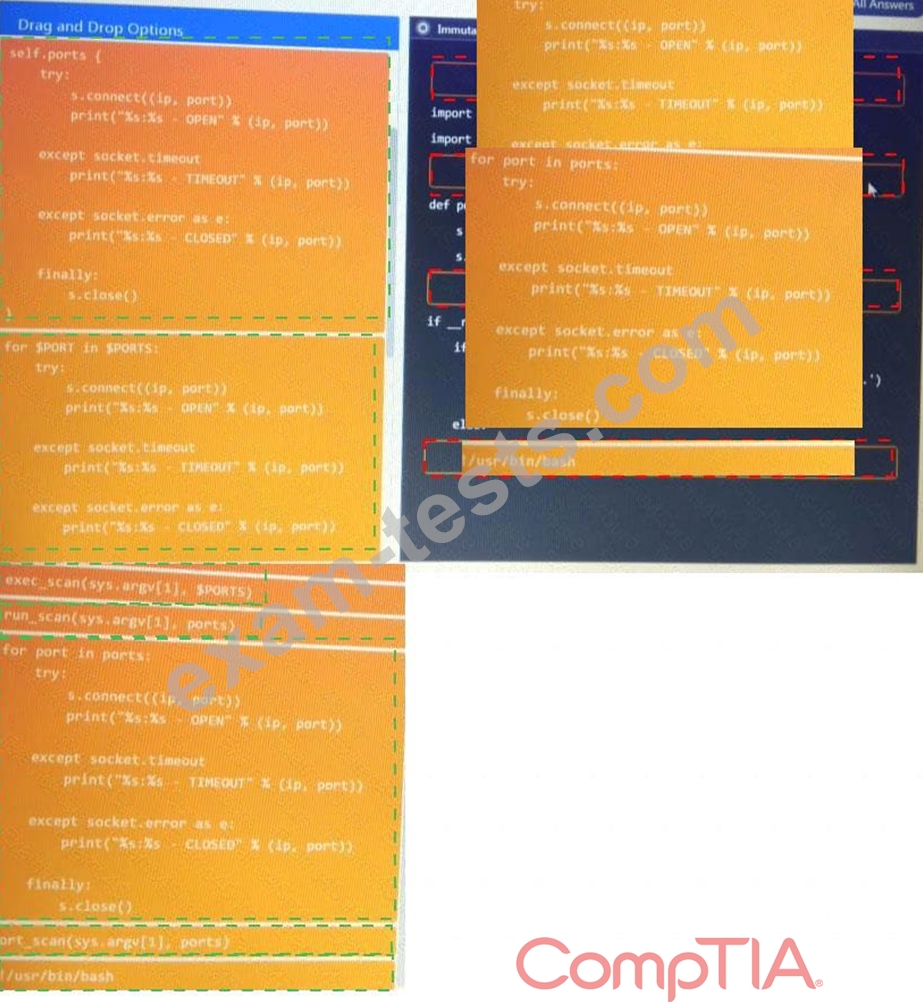
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
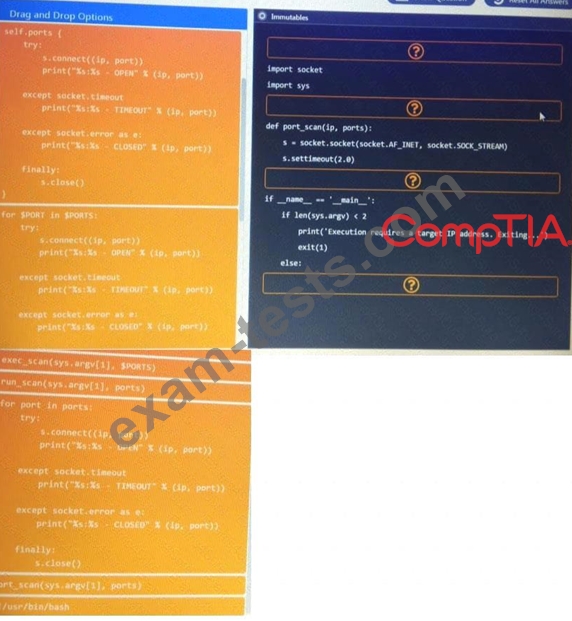
INSTRUCTIONS:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.