Question 81
A penetration tester is attempting to open a socket in a bash script but receives errors when running it. The current state of the relevant line in the script is as follows:
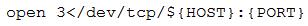
Which of the following lines of code would correct the issue upon substitution?
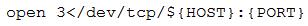
Which of the following lines of code would correct the issue upon substitution?
Question 82
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovering vulnerabilities, the company asked the consultant to perform the following tasks:
Code review
Updates to firewall settings
Which of the following has occurred in this situation?
Code review
Updates to firewall settings
Which of the following has occurred in this situation?
Question 83
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO)
Question 84
A financial institution is asking a penetration tester to determine if collusion capabilities to produce wire fraud are present. Which of the following threat actors should the penetration tester portray during the assessment?
Question 85
A constant wants to scan all the TCP Pots on an identified device. Which of the following Nmap switches will complete this task?

