Question 86
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz.
Which of the following registry changes would allow for credential caching in memory?
Which of the following registry changes would allow for credential caching in memory?
Question 87
Given the following Python script:
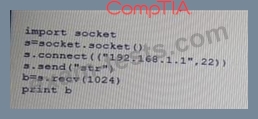
Which of the following actions will it perform?

Which of the following actions will it perform?
Question 88
A penetration tester is exploiting the use of default public and private community strings Which of the following protocols is being exploited?
Question 89
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
Question 90
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.)

