Question 81
A system administrator is implementing a security baseline template on a newly installed server.
Which of the following is a benefit of implementing the baseline?
Which of the following is a benefit of implementing the baseline?
Question 82
A company recently changed its security policy to allow access to only pre-approved websites and setup to occur without any end-user configuration. Which of the follow is the BEST configuration for implementing the new security policy?
Question 83
An employee on the Internet facing part of a company's website submits a 20-character phrase in a small textbox on a web form. The website returns a message back to the browser stating.

Of which of the following is this an example?

Of which of the following is this an example?
Question 84
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output:
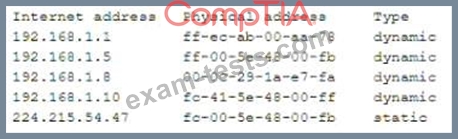
Which of the following BEST describes the attack the company is experiencing?

Which of the following BEST describes the attack the company is experiencing?
Question 85
Joe notices there are several user accounts on the local network generating spam with embedded malicious code.
Which of the following technical control should Joe put in place to BEST reduce these incidents?
Which of the following technical control should Joe put in place to BEST reduce these incidents?

