Question 76
The security administrator has installed a new firewall which implements an implicit DENY policy by default.
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
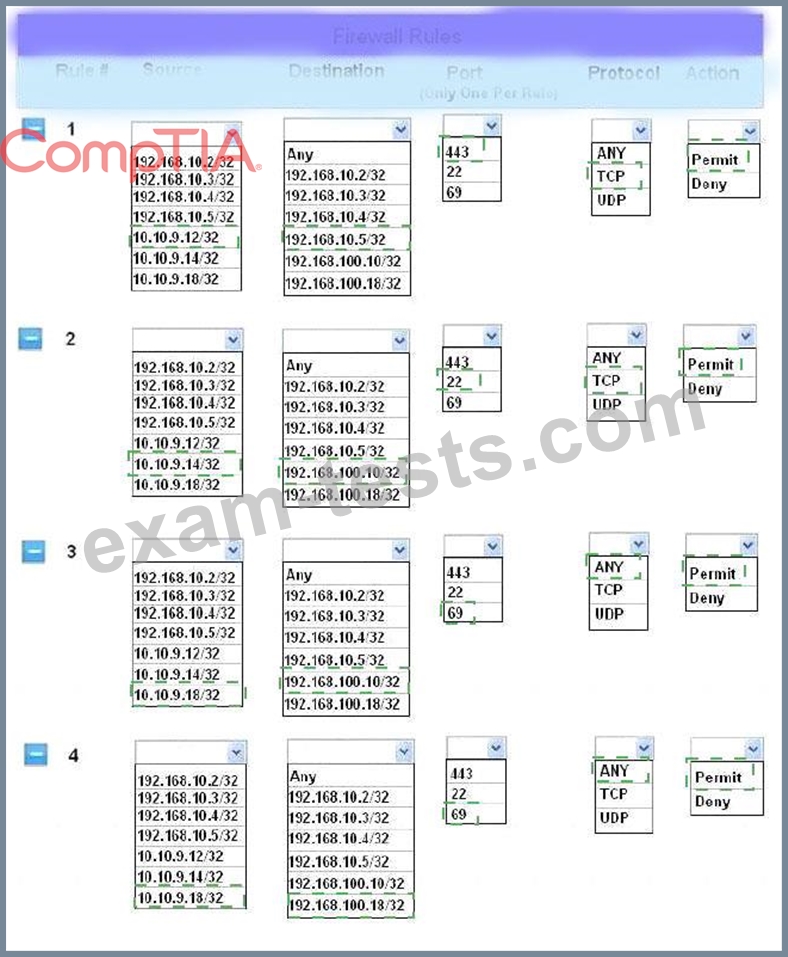
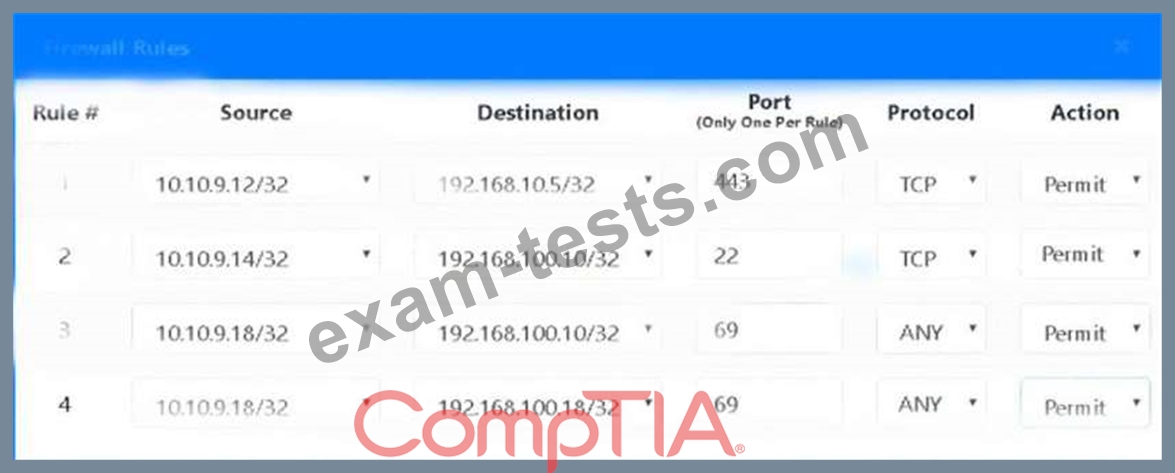
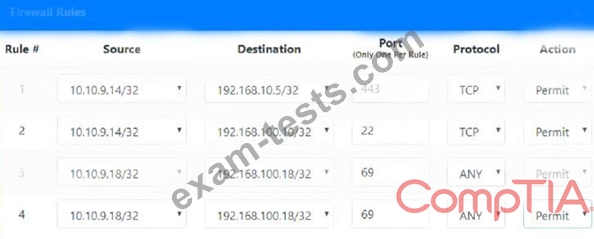
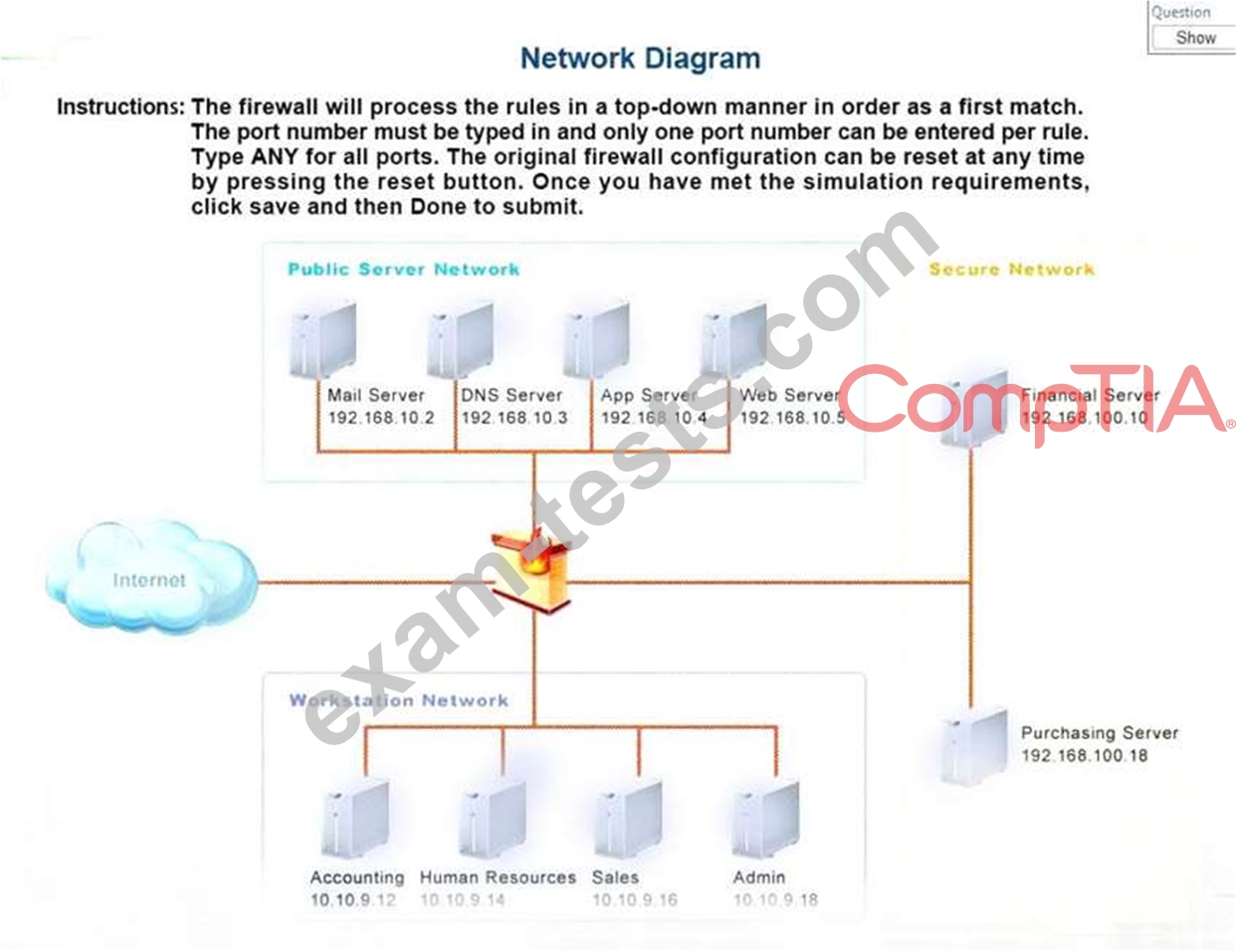
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
Hot Area:
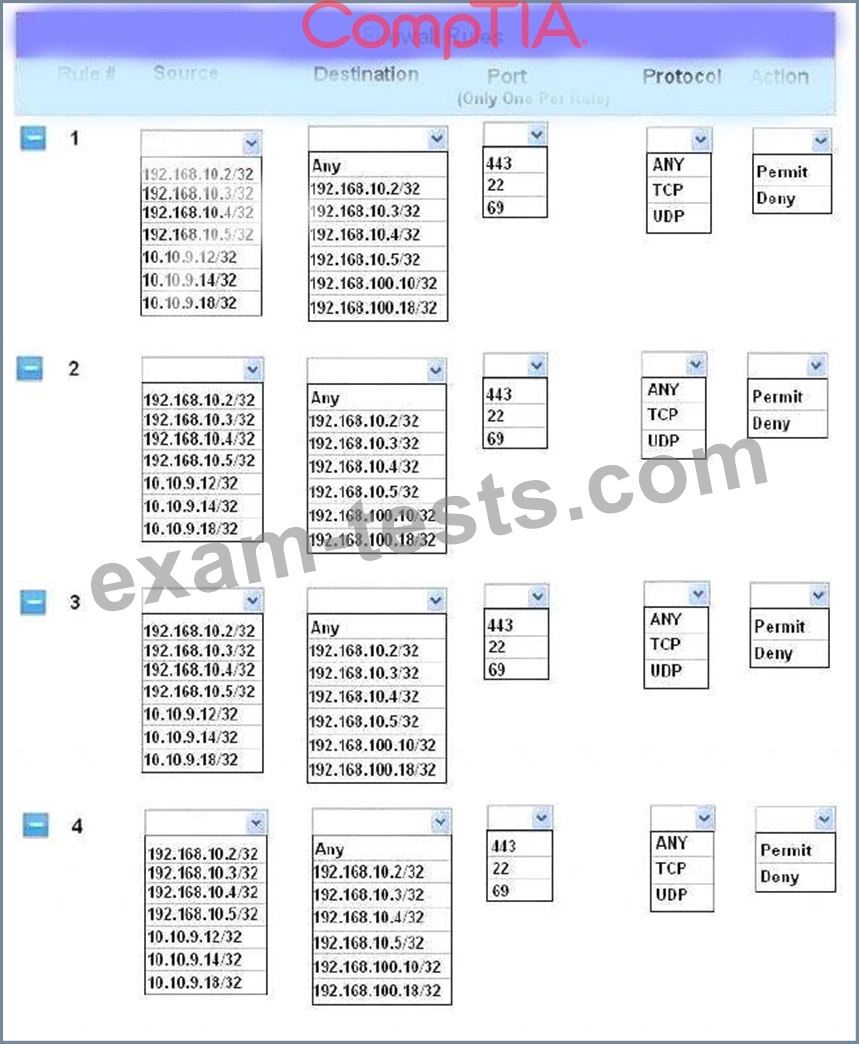
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.

Hot Area:

Question 77
A wireless network has the following design requirements:
*Authentication must not be dependent on enterprise directory service.
*It must allow backgroud reconenction for mobile users.
*It must not depend on user certificates.
Which of the following should be used in the design to meet the requirements? (Select Two)
*Authentication must not be dependent on enterprise directory service.
*It must allow backgroud reconenction for mobile users.
*It must not depend on user certificates.
Which of the following should be used in the design to meet the requirements? (Select Two)
Question 78
A user has attempted to access data at a higher classification level than the user's account is currently
authorized to access. Which of the following access control models has been applied to this user's
account?
authorized to access. Which of the following access control models has been applied to this user's
account?
Question 79
A forensic investigator has run into difficulty recovering usable files from a SAN drive. Which of the following SAN features might have caused the problem?
Question 80
A security analyst is updating a BIA document. The security analyst notices the support vendor's time to replace a server hard drive went from eight hours to two hours.
Given these new metrics, which of the following can be concluded? (Select TWO)
Given these new metrics, which of the following can be concluded? (Select TWO)