Question 466
The network information for a workstation is as follows:
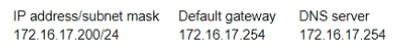
When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO)

When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO)
Question 467
Joe, an employee, wants to show his colleagues how much he knows about smartphones.
Joe demonstrates a free movie application that he installed from a third party on his corporate smartphone.
Joe's colleagues were unable to find the application in the app stores.
Which of the following allowed Joe to install the application? (Select two.)
Joe demonstrates a free movie application that he installed from a third party on his corporate smartphone.
Joe's colleagues were unable to find the application in the app stores.
Which of the following allowed Joe to install the application? (Select two.)
Question 468
An auditor wants to test the security posture of an organization by running a tool that will display the following:

Which of the following commands should be used?

Which of the following commands should be used?
Question 469
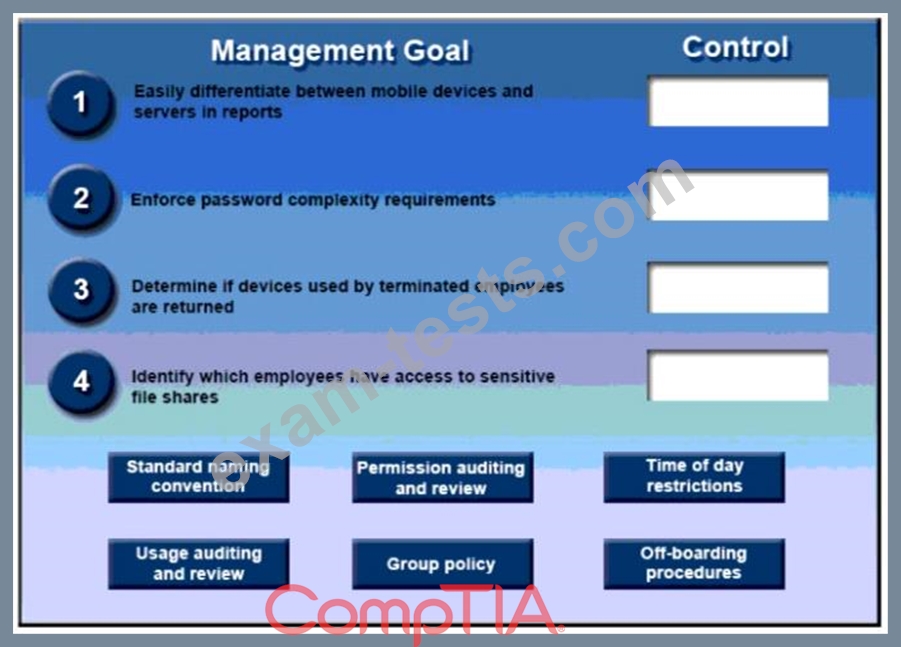
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.

Question 470
A system's administrator has finished configuring firewall ACL to allow access to a new web server.
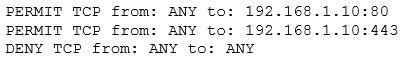
The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:

The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?

The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:

The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?


