Question 476
A recent review of accounts on various systems has found that after employees passwords are required to change they are recycling the same password as before. Which of the following policies should be enforced to prevent this from happening? (Select TWO)
Question 477
A security administrator is reviewing the following firewall configuration after receiving reports that users are unable to connect to remote websites:
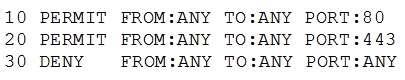
Which of the following is the MOST secure solution the security administrator can implement to fix this issue?

Which of the following is the MOST secure solution the security administrator can implement to fix this issue?
Question 478
An organization has the following password policies:
* Passwords must be at least 16 characters long.
* A password cannot be the same as any previous 20 passwords.
* Three failed login attempts will lock the account for five minutes.
* Passwords must have one uppercase letter, one lowercase letter, and one non-alphanumeric symbol.
A database server was recently breached, and the incident response team suspects the passwords were compromised. Users with permission on that database server were forced to change their passwords for that server. Unauthorized and suspicious logins are now being detected on a completely separate server. Which of the following is MOST likely the issue and the best solution?
* Passwords must be at least 16 characters long.
* A password cannot be the same as any previous 20 passwords.
* Three failed login attempts will lock the account for five minutes.
* Passwords must have one uppercase letter, one lowercase letter, and one non-alphanumeric symbol.
A database server was recently breached, and the incident response team suspects the passwords were compromised. Users with permission on that database server were forced to change their passwords for that server. Unauthorized and suspicious logins are now being detected on a completely separate server. Which of the following is MOST likely the issue and the best solution?
Question 479
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company's Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
Question 480
Which of the following attackers generally possesses minimal technical knowledge to perform advanced attacks and uses widely available tools as well as publicly available information?

