Question 111
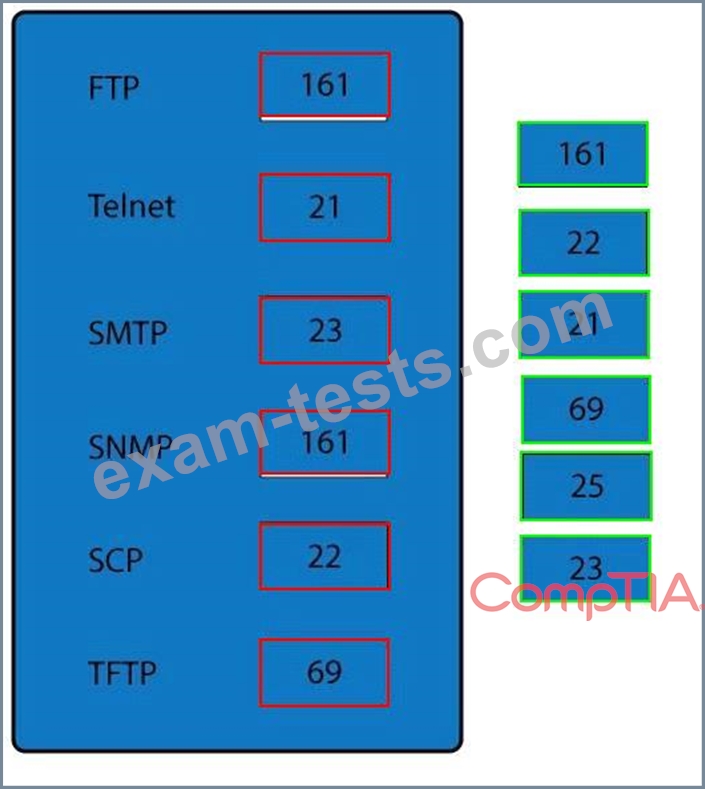
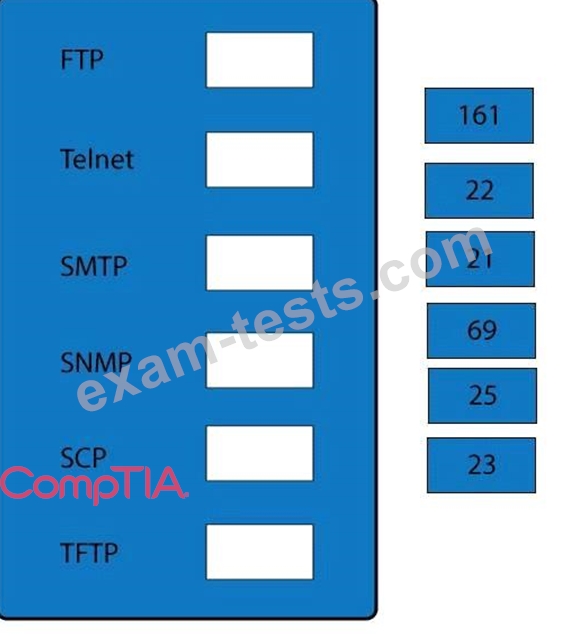
Drag and drop the correct protocol to its default port.

Question 112
A company recently updated its website to increase sales. The new website uses PHP forms for leads and provides a directory with sales staff and their phone numbers. A systems administrator is concerned with the new website and provides the following log to support the concern:
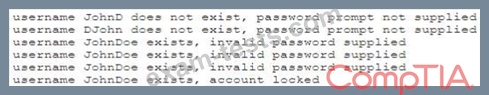
Which of the following is the systems administrator MOST likely to suggest to the Chief Information Security Officer (CISO) based on the above?

Which of the following is the systems administrator MOST likely to suggest to the Chief Information Security Officer (CISO) based on the above?
Question 113
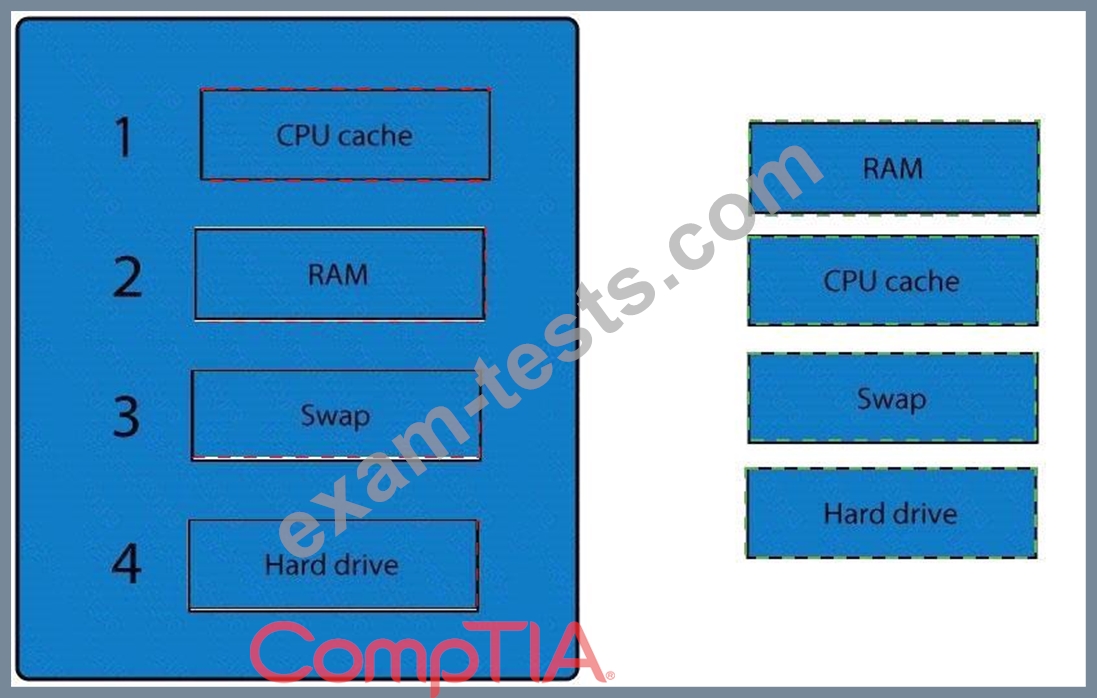
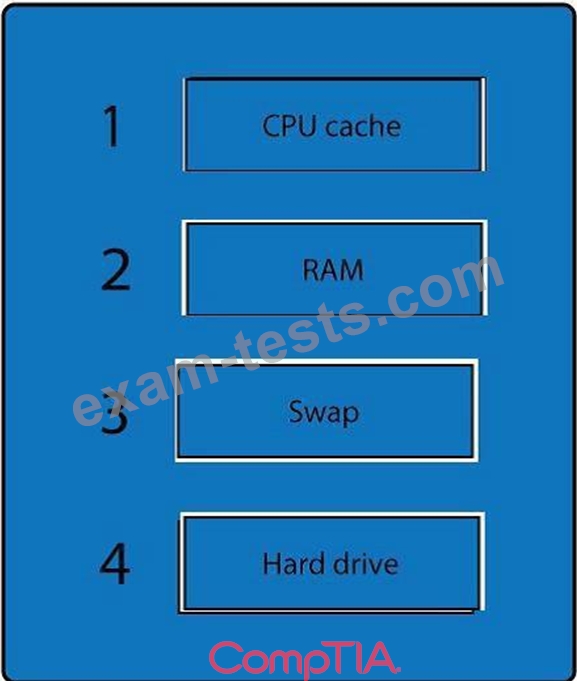
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
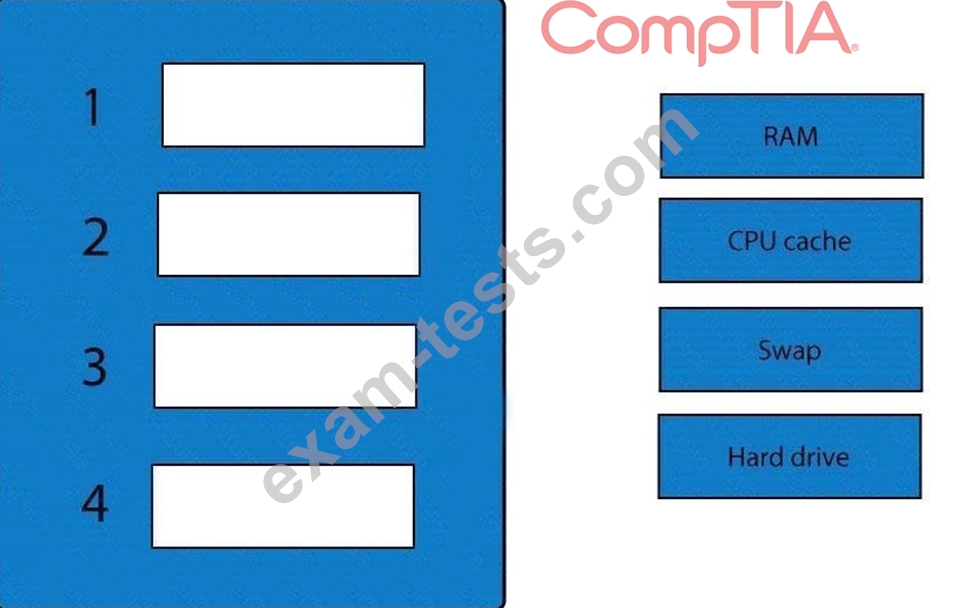

Question 114
A security manager is preparing the training portion of an incident plan. Which of the following job roles should receive training on forensics, chain of custody, and the order of volatility?
Question 115
A user clicked an email link that led to a website that infected the workstation with a virus.
The virus encrypted all the network shares to which the user had access. The virus was not detected or blocked by the company's email filter, website filter, or antivirus. Which of the following describes what occurred?
The virus encrypted all the network shares to which the user had access. The virus was not detected or blocked by the company's email filter, website filter, or antivirus. Which of the following describes what occurred?