Question 126
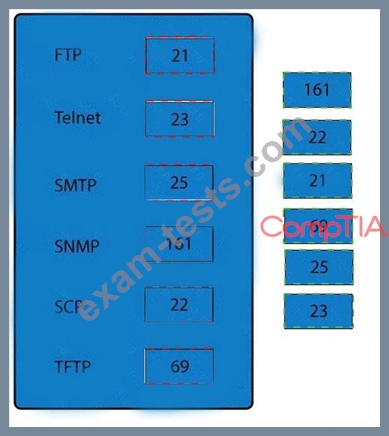
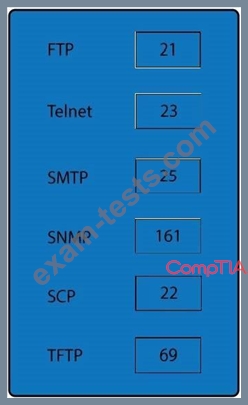
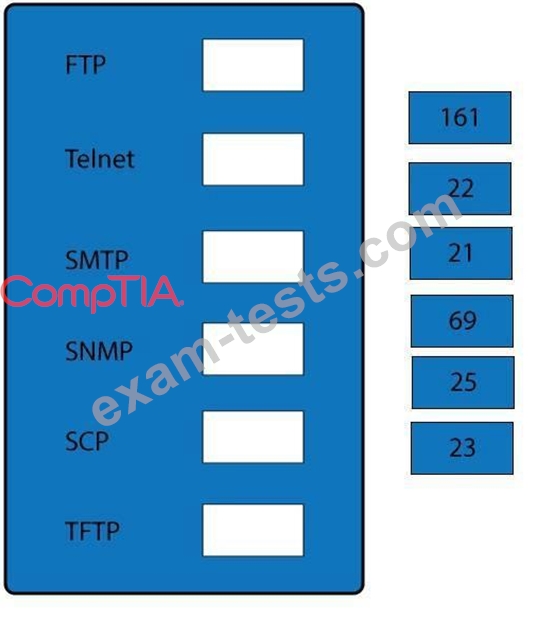
Drag and drop the correct protocol to its default port.

Question 127
A security administrator is reviewing the following information from a file that was found on a compromised host:
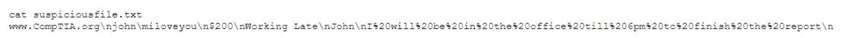
Which of the following types of malware is MOST likely installed on the compromised host?

Which of the following types of malware is MOST likely installed on the compromised host?
Question 128
Which of the following impacts MOST likely results from poor exception handling?
Question 129
Joe, a technician, is working remotely with his company provided laptop at the coffee shop near his home.
Joe is concerned that another patron of the coffee shop may be trying to access his laptop.
Which of the following is an appropriate control to use to prevent the other patron from accessing Joe's
laptop directly?
Joe is concerned that another patron of the coffee shop may be trying to access his laptop.
Which of the following is an appropriate control to use to prevent the other patron from accessing Joe's
laptop directly?
Question 130
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
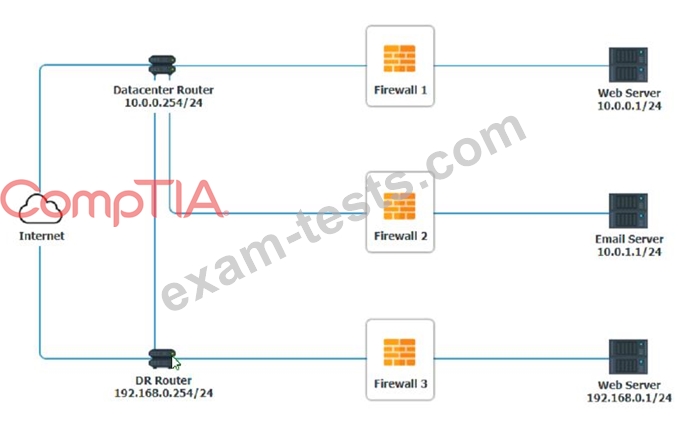
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
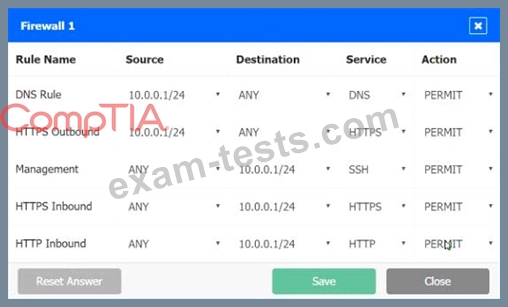
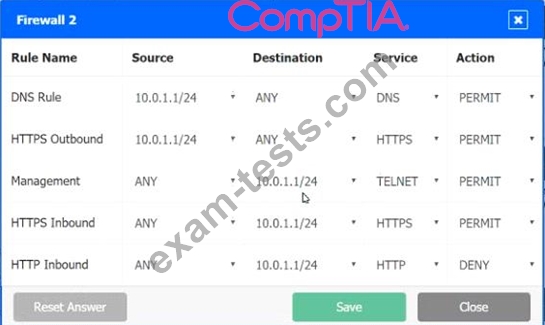
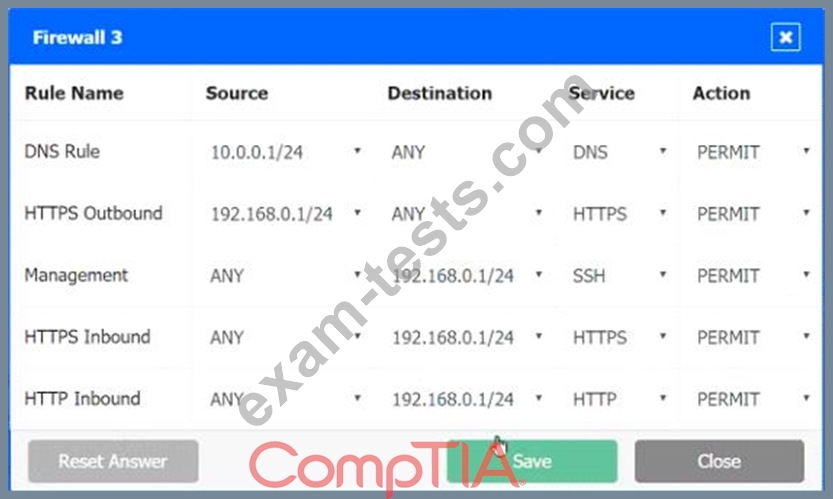

INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.