Question 116
A system's administrator has finished configuring firewall ACL to allow access to a new web server.
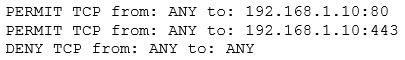
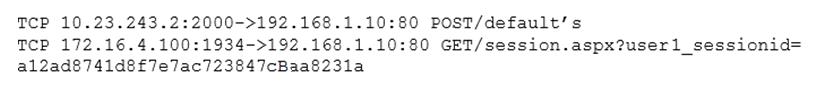
The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:
The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?

The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:

The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?
Question 117
A technician is investigating a report of unusual behavior and slow performance on a company-owned laptop.
The technician runs a command and reviews the following information:
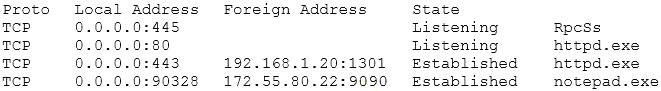
Based on the above information, which of the following types of malware should the technician report?
The technician runs a command and reviews the following information:

Based on the above information, which of the following types of malware should the technician report?
Question 118
An analyst is concerned about data leaks and wants to restrict access to Internet services to authorized users only. The analyst also wants to control the actions each user can perform on each service Which of the following would be the BEST technology for me analyst to consider implementing?
Question 119
Which of the following types of penetration test will allow the tester to have access only to password hashes prior to the penetration test?
Question 120
A development team has adopted a new approach to projects in which feedback is iterative and multiple iterations of deployments are provided within an application's full life cycle. Which of the following software development methodologies is the development team using?

