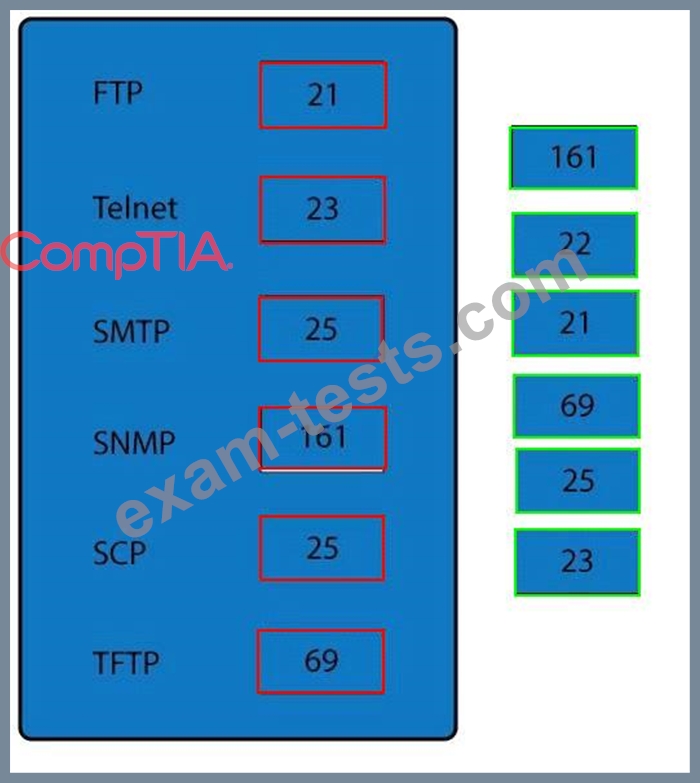
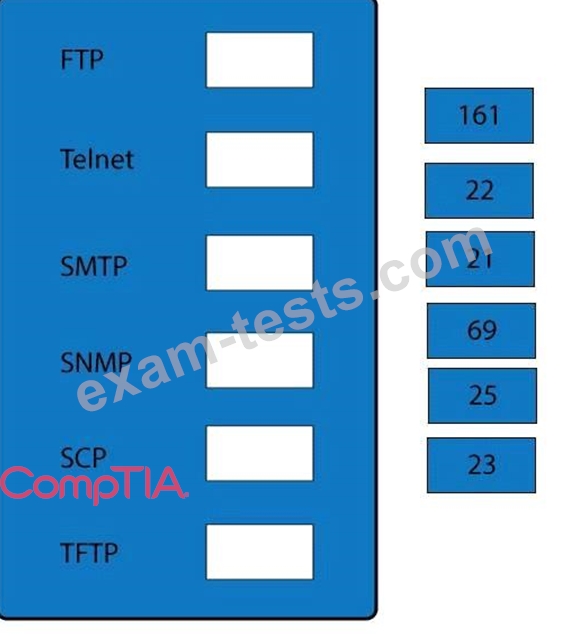
Question 121
Drag and drop the correct protocol to its default port.

Question 122
A network engineer needs to allow an organization's users to conned their laptops to wired and wireless networks from multiple locations and facilities, while preventing unauthorized connections to the corporate networks. Which of the following should be Implemented to fulfill the engineer's requirements?
Question 123
A company hired a firm to test the security posture of its database servers and determine if any vulnerabilities can be exploited. The company provided limited imformation pertaining to the infrastructure and database server. Which of the following forms of testing does this BEST describe?
Question 124
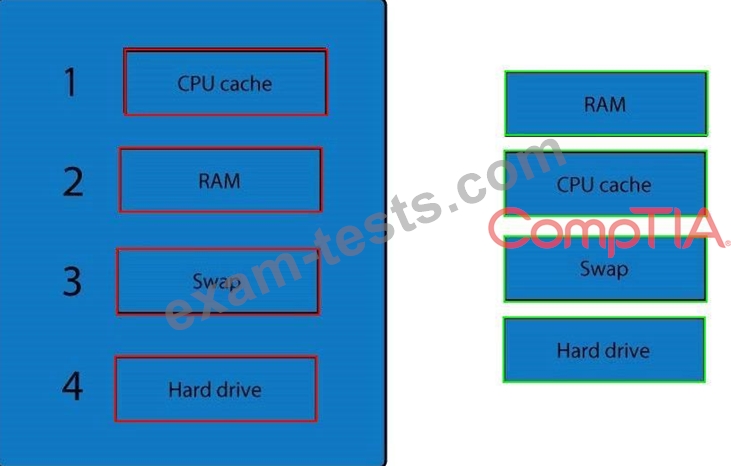
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
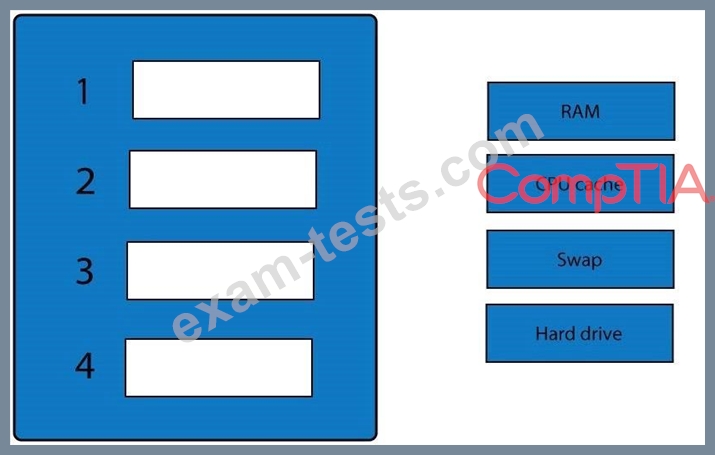

Question 125
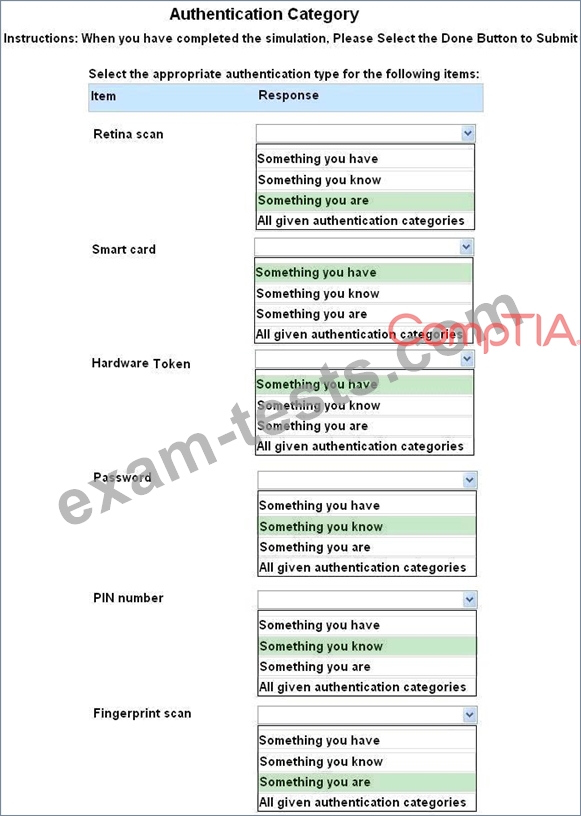
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit.

Instructions: When you have completed the simulation, please select the Done button to submit.